Hello everyone,
I created Site to Site IPSec VPN Connections before for a customer, which worked just fine. Strangely I encountered the following Problem with the latest connection and I couldn't find any problems regarding the configuration. Maybe you can help me in this case.
I do not have control over the remote appliance.
We have three local subnets and one remote network, which is basically just one IP, but configured as a /32 network.
We configured the IPSec VPN on both sides and exchanged PSKs and the tunnel was immediately connected and the three SAs were established.
IPSec-Policy:
IKEv2 Mainmode
Phase1:
DH-Group14
AES256/SHA256
Phase2:
DH-Group14
AES256/SHA256
DPD deactivated
IPSec-Connection in the XG:
Site2Site
initiate connection
Authentication: PSK
local/remote ID Type: IP-Address with the local and remote gateway.
No NAT on both sides
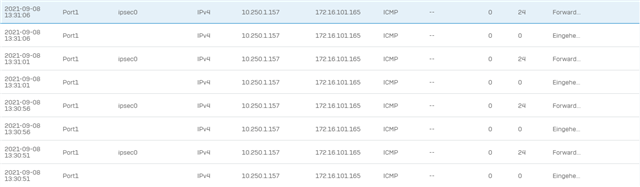
Routes are set to the virtual ipsec adapter correctly according to advanced shell, when IPSec-Connection is enabled. But I can't ping the remote subnet/IP-Address.
When I try a traceroute either from the XG Webadmin or one of the local subnets while connected, the first hop is beeing routed to the remote Gateway-Address (the remote external Interface, that is beeing used to establish the tunnel), which I just can't get my head around. I can't get the connection to work properly.
I'd appreciate any help!
Thanks in advance,
Kind Regards,
Oliver
This thread was automatically locked due to age.