Hello to the community,
I found some discussions on this topic but as none lead me to success so far, hopefully someone can help me with my topic.
Scenario:
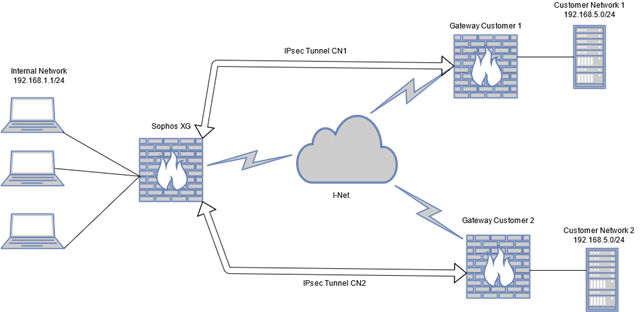
Sophos XG (18.0.5 MR5) with several IPsec site-to-site tunnels
Two of the remote networks (name them "CN1" and "CN2") have the same IP Range (e.g. 192.168.5.0)
I have no configuration options on the remote side, so the whole NATing has to be done on the XG
Goal:
CN2 should be made available as 192.168.10.0
So when I want to connect to 192.168.5.40 on this network, on my side I initiate a connection to the "fake address" 192.168.10.40
This should work for the whole network of CN2.
What I've tried so far:
Created a DNAT Rule, which translates 192.168.10.0 requests from my local network to CN2=192.168.5.0
As it is not possible to use a network in "translated destination", I created network ranges for local (source) net, real target net (CN2) and "fake" target net
In the above DNAT rule used only these ranges, because in another post it was recommended to do so.
This rule does not work.
When I observe the tunnel via console by using "tcpdump" and send a Ping to 192.168.10.40, this doesn't hit the tunnel to CN2.
Even more strange: when I send a Ping to 192.168.5.40, it shows up on the tcpdump of CN2.
Any help to resolve this is appreciated.
Regards
RanX
This thread was automatically locked due to age.