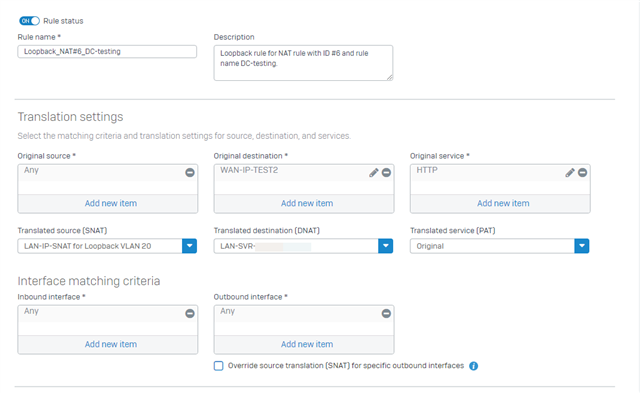
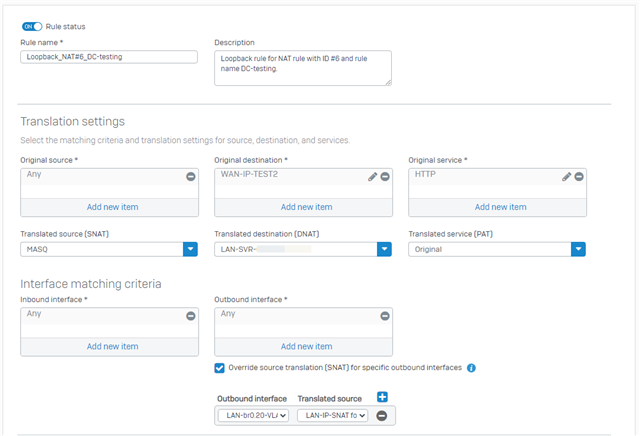
We are looking to deploy an HA pair of XGS2100 firewalls to our data centre. My issue is I cannot get a loopback NAT to work when I am starting the conversation from the same zone as the destination server is in. IF the loopback is to a different zone all is good.
I have googled this for hours and spent hours on the phone with support to no avail. I do have a support ticket open already but I hoping someone might have some additional insight into this.
The Firewall currently have 18.5 MR1 installed.
This thread was automatically locked due to age.