Hello,
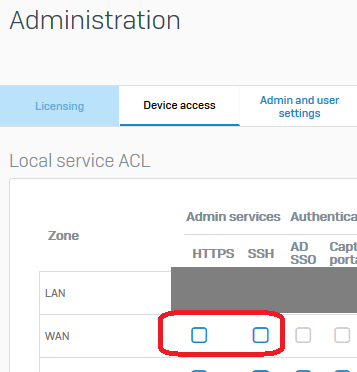
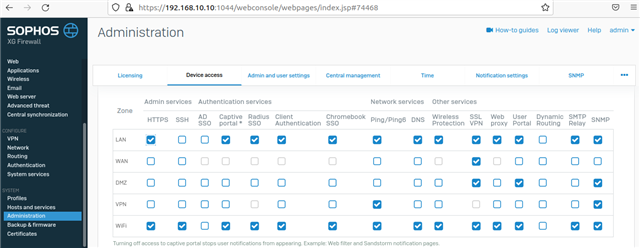
We disabled ssh access on WAN port and LAN port, but we get mail notification of many different public IP try to login via ssh..
Below notification which we gets.
Message:
User 'root' failed to login from '61.177.173.16' using ssh because of wrong credentials
Message:
User 'admin' failed to login from '107.189.2.212' using ssh because of wrong credentials
Message:
User 'pi' failed to login from '91.167.123.220' using ssh because of wrong credentials
if we disabled ssh on wan side and LAN side, why someone to get access of ssh?
Anybody can help me such type of attack.
This thread was automatically locked due to age.