In the ongoing saga of trying to clean-up our broken AWS S2S VPN tunnels this past weekend, we rebuilt them and finally got them working via BGP. Unfortunately now, we're left with a new problem. The XG itself can't authenticate with our AD DC's located in AWS, meaning services such as VPN aren't working.
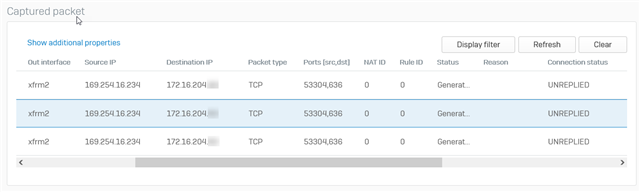
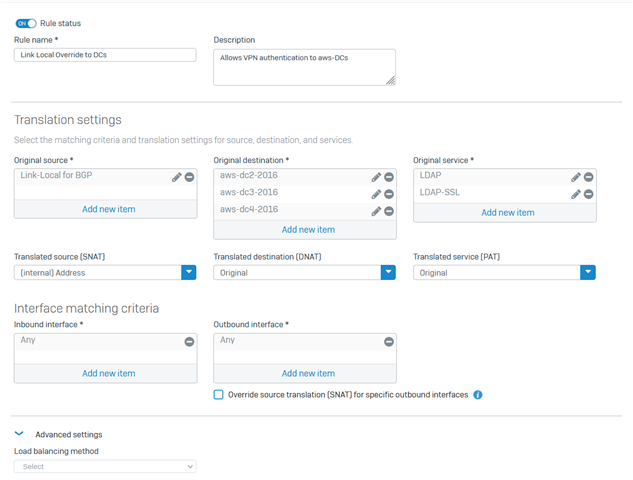
This appears to be a problem with a NAT rule.The issue appears to be related to the fact that when the firewall attempts to contact the DCs to authenticate, the address they are coming from is a link-local address (whichever is the current active tunnel). Setting up a NAT rule so that link-local will SNAT to the internal IP address of the XG itself doesn't seem to work (0 connections match that rule).
This thread was automatically locked due to age.


