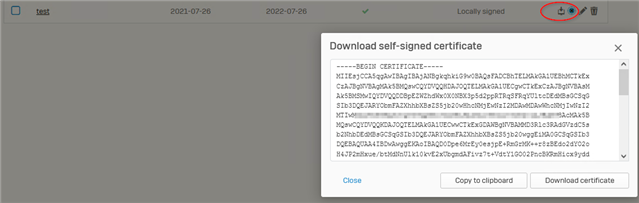
Since SFOS 18.0.5 (18 MR5) it is no longer possible to download self-signed certificates as .p12-certificate (certificate with private-key).
It is only possible to download the certificate as .crt without private-key.
Does anyone have an idea how to do that with 18 MR5?
This thread was automatically locked due to age.


