Good Morning,
i am looking for a routing solution for my network to a remote location.
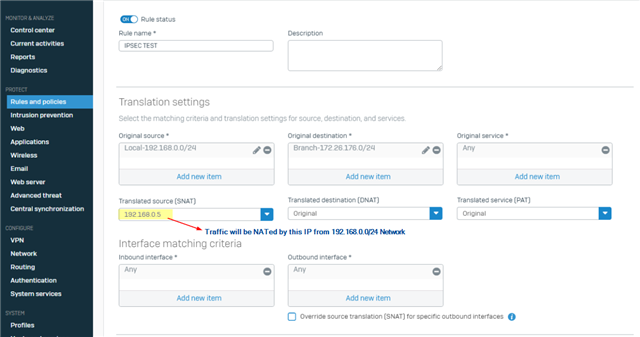
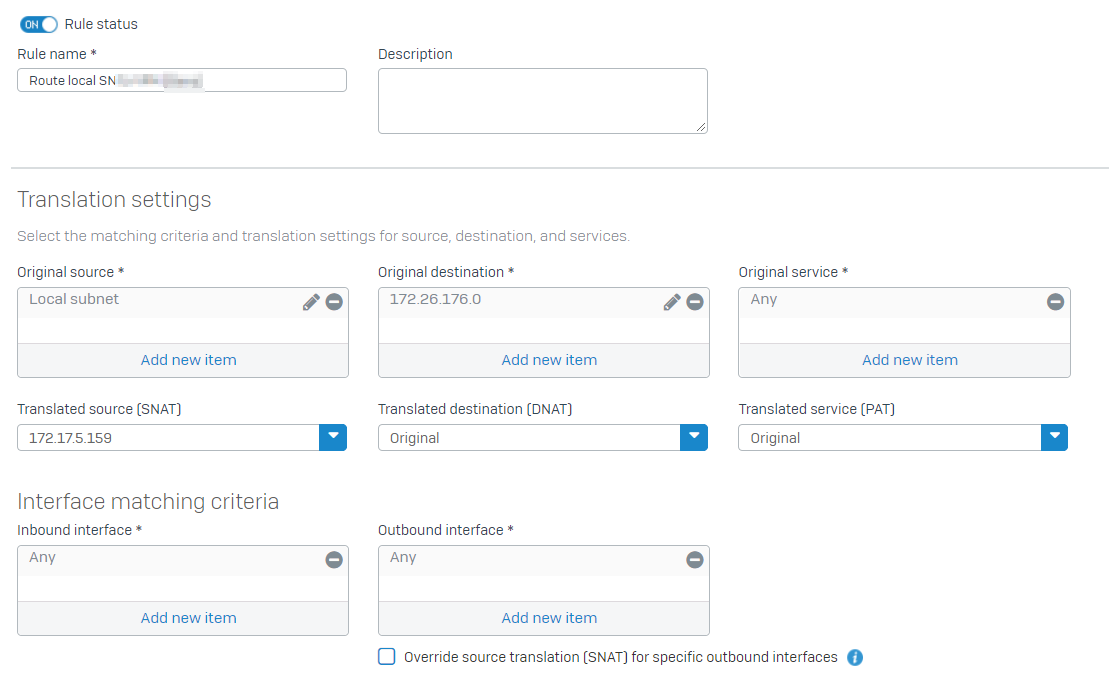
We use a Sophos XG 18.0.5 MR-5 and i use a Site2Site Tunnel between two Subnets.
Head Office 172.17.5.0/24 and BO 172.26.176.0
Our local Subnet has 192.168.0.0/24 and 172.17.5.0/24 is VLAN 5. I have a routing from VLAN 172.17.5.0/24 to BO that´s fine.
I thought, if there might be an easyway to route the local Subnet 192.168.0.0/24 to the BO without the use of the VLAN oder changing the firewalls in BO.
In a fortinet Manual i found some option to do Site2Site Routing with a overlapping (same) Subnet in HO/BO.
They use a NAT Translation in HO and BO.
Is there any way to setup somethin in sophos?
Thanks
Jürgen
This thread was automatically locked due to age.