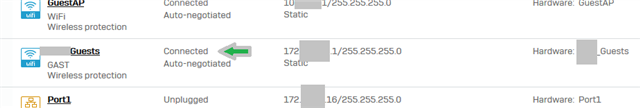
We updated WiFi AP Firmware 3 days ago. on one location with some AP55c clients connecting to a WiFi will not get IP addresses. I cannot even see the DHCP requests with packet capture.
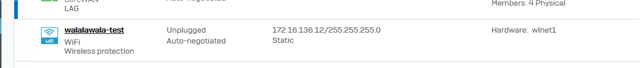
I noticed the WiFi interface is shown as unplugged. When I noticed the issue, the Interface did not even have a MAC address (00:00:00:00:00:00).
So I edited, disabled, enabled the SSID and the interface. It remains in unplugged status. No luck, at least it got MAC address again by those changes.
Unplugged and no MAC Address:

After changing and re-applying settings back to original values:
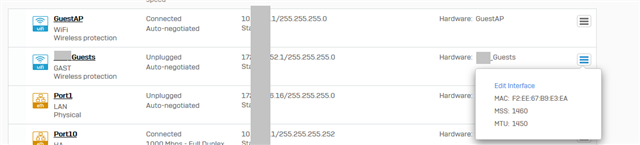
XXX_Guests Link encap:Ethernet HWaddr F2:EE:67:B9:E3:EA
inet addr:172.xxx.xxx.1 Bcast:172.xxx.252.255 Mask:255.255.255.0
inet6 addr: fe80::a86d:xxxxxxxxxxxxxx:1bb1/64 Scope:Link
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:6326211 errors:0 dropped:0 overruns:0 frame:0
TX packets:6022720 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:5041929744 (4.6 GiB) TX bytes:4307225067 (4.0 GiB)
any help on this please?
update 7.7.2021: noticed missing vxlan adapters on the HA nodes that came up after reboot of the nodes. See comments below.
This thread was automatically locked due to age.