Good Morning,
I am currently trying to block various clients from accessing the Internet.
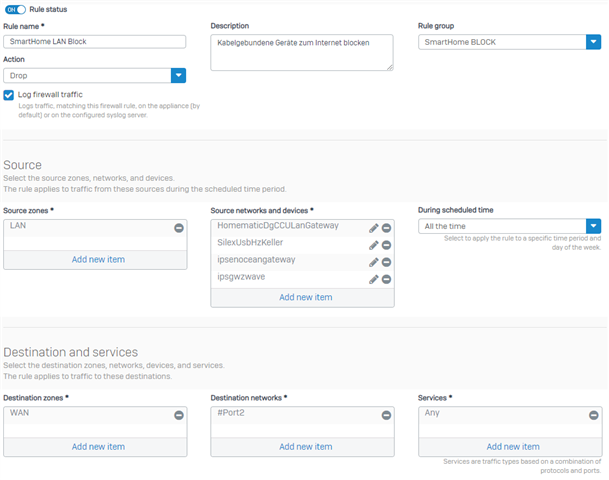
Unfortunately, I can't get these clients blocked. I have created a firewall rule
In the SG I understood that so far, in the XG I am totally confused. Then the question arises for me, why can I link the rule with a NAT rule?
Can someone explain the connections to me to some extent?
Thanks and regards
This thread was automatically locked due to age.


