Hi,
I want to configure my policies in a way that only proxied connections are allowed from lan to wan. I don't want a transparent proxy.
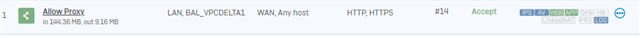
I set up the proxy within my Sophos to accept connections on port 8080 from lan.
I set up a new policy group at the top with two rules:
- Allow traffic from lan to Sophos port 8080
- Reject all traffic from lan to wan
I setup a browser on my client to use the proxy on port 8080 on the Sophos.
I expected to be able to visit websites. I'm greeted with a webpage from the sophos proxy stating the the website cannot be reached.
If I add another policy allowin port 80 and 443 from lan to wan (as suggested by the docs) I can reach the websites without using a proxy. I did not find any documentation on how to achieve the wanted outcome.
Does anybody in the community have an idea what I did wrong?
Cheers,
Nicki
This thread was automatically locked due to age.