I'm noticing a strange IP address on the network: 192.168.99.76. I can't find 192.168.99 anywhere in the SFOS.
But the mystery is even deeper because it appears that packets to this IP are being forwarded to the WAN. I think. But it's confusing...
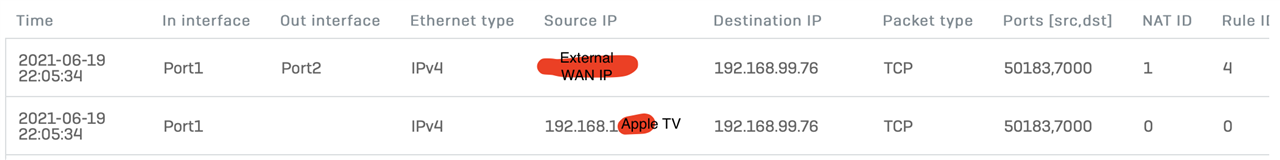
I captured packets and this is one of those strange situations where I can't quite understand what's going on. There are always two TCP packets together:
1. Has the source IP of the AppleTV port 50183 and the destination is 192.168.99.76 port 7000. The IPv4 Checksum is always the same, though I can see slight changes in the body. The In interface is Port 1 (which connects to the APX), no Out interface is listed.
2. Has the source of the public IP of the WAN port (Port 2) and port 50183 and the destination is again 192.168.99.76 port 7000. The IPv4 Checksum is always the same, though I can see slight changes in the body. The In interface is Port 1 and the Out interface is Port 2.
The checksums of the two packets are different and their content looks different. (All 64 bytes total length.) Though as mentioned the Packet #1's all have the same checksum, and the Packet #2's all have the same checksum.
It feels like this is one packet caught at two points in time, going from the AppleTV wirelessly to the APX into Port 1 and out of Port 2 to the Internet.. (Except for the differing checksums.) But it's very confusing. And 192.168.99 is a private network so should not every go out Port 2 (WAN), right?
The second packer which has an Out Interface Port of 2 (WAN) also has a Firewall Rule of 4, which is the LAN/Any to WAN/Any rule. So I think it's not being dropped.
This thread was automatically locked due to age.