Hi,
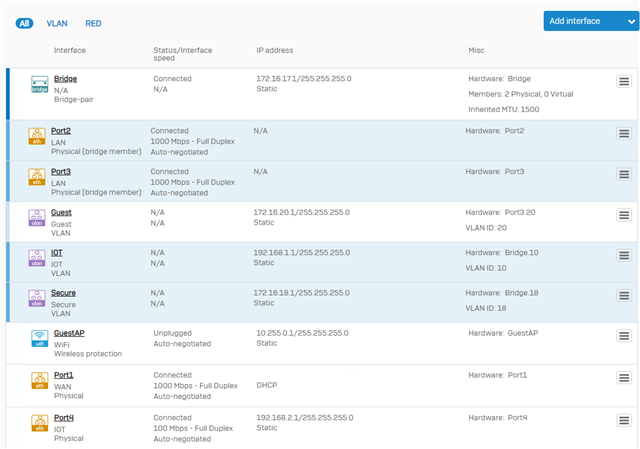
So I have two physical interfaces and want to have the native VLAN and VLAN 10 on both of them. The first interface is connected to an wireless AP and the second is connected to a switch. The goal here is that wireless devices on VLAN 10 should be able to talk to wired devices connected to the switch on VLAN 10. VLAN 10 is for IOT-devices.
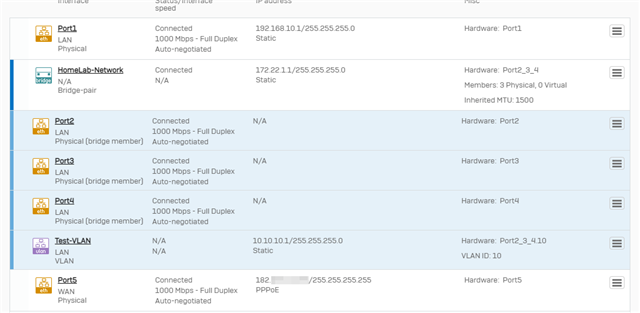
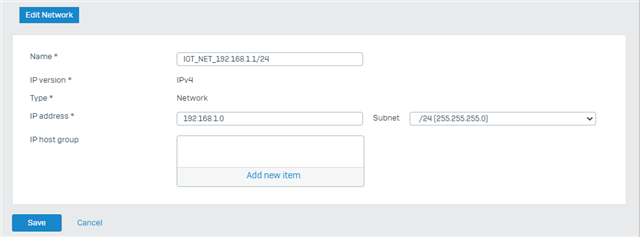
To achieve this I created a bridge with the two physical interfaces as members. I then added VLAN 10 to that bridge. I also set up two DHCP-servers, one for each VLAN.
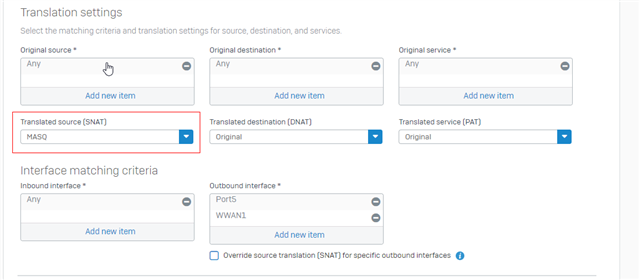
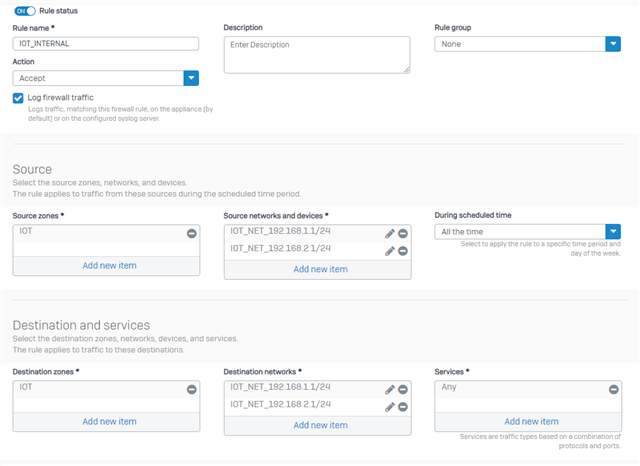
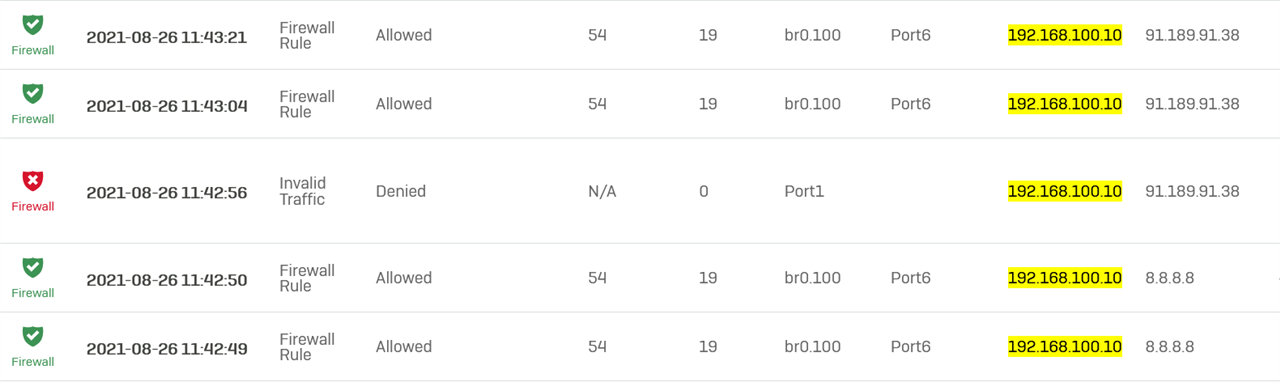
Devices connected to either the VLAN 10 SSID or a VLAN 10 port in the switch are assigned the correct IP-addresses. I've setup a firewall rule that allows any host in IOT-zone to access the WAN-zone.
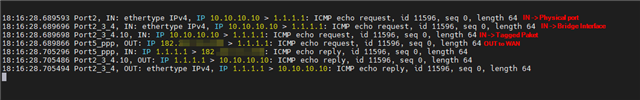
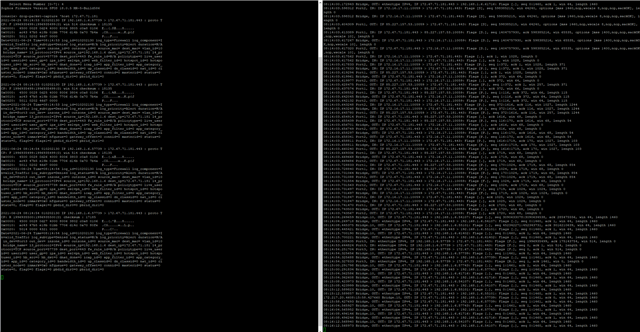
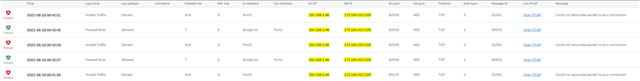
The problem is that devices on VLAN 10 cant access the internet. Looking in the log, some packets are going thru but some are labelled "Could not associate packet to any connection." and are denied. Different packages with same source and destination IP are sometimes allowed and sometimes denied. The ones that are allowed have "in interface: bridge.10." The ones that are denied have "in interface: port2.".
Devices not on VLAN 10 work just fine.
I'm on version SFVH (SFOS 18.0.5 MR-5-Build586).
Big thanks for any advice.
This thread was automatically locked due to age.