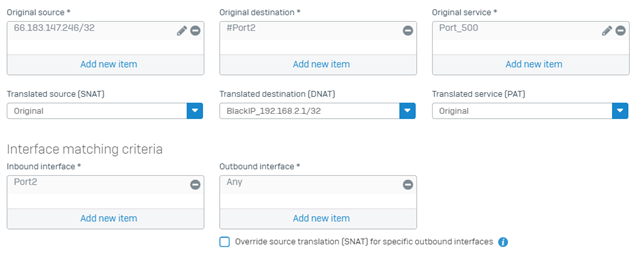
Hello. We have a FW rule to block all/all/all traffic coming from specific IP addresses. It seems to work for HTTPS attempts etc. but IPSec login attempts are not blocked. How do we block Sophos Connect VPN login attempts from specific IP addresses?
This thread was automatically locked due to age.