hello everyone
i have set up ssl vpn for over a year and everything is working fine
suddenly i couldnt connect anymore although i hav`t change anything
i have tried so far to delete all configuration and reconfigure ,
regenerate all acertificates (default and SSL)
and even rebooted xg with factory settings without any luck
and i still get error TLS HANDSHAKE ERROR
this is log from vpn client
Sat May 01 01:42:31 2021 OpenVPN 2.3.8 i686-w64-mingw32 [SSL (OpenSSL)] [LZO] [IPv6] built on Jul 3 2017
Sat May 01 01:42:31 2021 library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.09
Enter Management Password:
Sat May 01 01:42:31 2021 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Sat May 01 01:42:31 2021 Need hold release from management interface, waiting...
Sat May 01 01:42:31 2021 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Sat May 01 01:42:31 2021 MANAGEMENT: CMD 'state on'
Sat May 01 01:42:31 2021 MANAGEMENT: CMD 'log all on'
Sat May 01 01:42:31 2021 MANAGEMENT: CMD 'hold off'
Sat May 01 01:42:31 2021 MANAGEMENT: CMD 'hold release'
Sat May 01 01:42:33 2021 MANAGEMENT: CMD 'username "Auth" "1"'
Sat May 01 01:42:33 2021 MANAGEMENT: CMD 'password [...]'
Sat May 01 01:42:33 2021 WARNING: No server certificate verification method has been enabled. See openvpn.net/howto.html for more info.
Sat May 01 01:42:34 2021 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sat May 01 01:42:34 2021 UDPv4 link local: [undef]
Sat May 01 01:42:34 2021 UDPv4 link remote: [AF_INET]**xG Public IP**:8443
Sat May 01 01:42:34 2021 MANAGEMENT: >STATE:1619826154,WAIT,,,,,,
Sat May 01 01:42:34 2021 MANAGEMENT: >STATE:1619826154,AUTH,,,,,,
Sat May 01 01:42:34 2021 TLS: Initial packet from [AF_INET]**xG Public IP**:8443, sid=aa8e3f95 67af15ce
Sat May 01 01:42:34 2021 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sat May 01 01:43:34 2021 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sat May 01 01:43:34 2021 TLS Error: TLS handshake failed
Sat May 01 01:43:34 2021 SIGUSR1[soft,tls-error] received, process restarting
Sat May 01 01:43:34 2021 MANAGEMENT: >STATE:1619826214,RECONNECTING,tls-error,,,,,
Sat May 01 01:43:34 2021 Restart pause, 2 second(s)
Sat May 01 01:43:36 2021 WARNING: No server certificate verification method has been enabled. See openvpn.net/howto.html for more info.
Sat May 01 01:43:36 2021 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sat May 01 01:43:36 2021 UDPv4 link local: [undef]
Sat May 01 01:43:36 2021 UDPv4 link remote: [AF_INET]**xG Public IP**:8443
Sat May 01 01:43:36 2021 MANAGEMENT: >STATE:1619826216,WAIT,,,,,,
Sat May 01 01:43:36 2021 MANAGEMENT: >STATE:1619826216,AUTH,,,,,,
Sat May 01 01:43:36 2021 TLS: Initial packet from [AF_INET]**xG Public IP**:8443, sid=580a9e30 4cd32200
Sat May 01 01:44:06 2021 SIGTERM received, sending exit notification to peer
Sat May 01 01:44:07 2021 SIGTERM[soft,exit-with-notification] received, process exiting
Sat May 01 01:44:07 2021 MANAGEMENT: >STATE:1619826247,EXITING,exit-with-notification,,,,,
and this is tcpdump from xg for port 8443
Sophos Firewall
===============
(C) Copyright 2000-2019 Sophos Limited and others. All rights reserved.
Sophos is a registered trademark of Sophos Limited and Sophos Group.
All other product and company names mentioned are trademarks or registered
trademarks of their respective owners.
For End User License Agreement - www.sophos.com/.../sophos-end-user-license-agreement.aspx
NOTE: If not explicitly approved by Sophos support, any modifications
done through this option will void your support.
SFVH_SO01_SFOS 17.5.9 MR-9.HF062020.1# tcpdump "port 8443"
tcpdump: Starting Packet Dump
01:47:36.250551 Port2, IN: IP host.**Client Public IP**.nile-online.net.58591 > host-**XG Public IP**.tedata.net.8443: UDP, length 14
01:47:36.253048 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58591: UDP, length 26
01:47:38.591921 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58591: UDP, length 14
01:47:42.099910 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58591: UDP, length 14
01:47:50.267920 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58591: UDP, length 14
01:48:06.535971 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58591: UDP, length 14
01:48:38.997024 Port2, IN: IP host.**Client Public IP**.nile-online.net.58598 > host-**XG Public IP**.tedata.net.8443: UDP, length 14
01:48:38.998304 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58598: UDP, length 26
01:48:40.187902 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58598: UDP, length 14
01:48:44.939807 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58598: UDP, length 14
01:48:52.571939 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58598: UDP, length 14
01:49:08.031965 Port2, OUT: IP host-**XG Public IP**.tedata.net.8443 > host.**Client Public IP**.nile-online.net.58598: UDP, length 14
and this is tail ssl log from advanced shell
Sat May 1 01:52:01 2021 us=78439 [8728] MULTI: multi_create_instance called
Sat May 1 01:52:01 2021 us=78576 [8728] ::ffff:62.114.212.210 Re-using SSL/TLS context
Sat May 1 01:52:01 2021 us=78642 [8728] ::ffff:62.114.212.210 LZO compression initialized
Sat May 1 01:52:01 2021 us=78807 [8728] ::ffff:62.114.212.210 Control Channel MTU parms [ L:1570 D:138 EF:38 EB:0 ET:0 EL:0 ]
Sat May 1 01:52:01 2021 us=78851 [8728] ::ffff:62.114.212.210 Data Channel MTU parms [ L:1570 D:1450 EF:70 EB:135 ET:0 EL:0 AF:3/1 ]
Sat May 1 01:52:01 2021 us=78946 [8728] ::ffff:62.114.212.210 Local Options String: 'V4,dev-type tun,link-mtu 1570,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-server'
Sat May 1 01:52:01 2021 us=79001 [8728] ::ffff:62.114.212.210 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1570,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-client'
Sat May 1 01:52:01 2021 us=79051 [8728] ::ffff:62.114.212.210 Local Options hash (VER=V4): '00bc425f'
Sat May 1 01:52:01 2021 us=79093 [8728] ::ffff:62.114.212.210 Expected Remote Options hash (VER=V4): 'ec542dd5'
Sat May 1 01:52:01 2021 us=79189 [8728] ::ffff:62.114.212.210 UDPv6 READ [14] from [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Sat May 1 01:52:01 2021 us=79250 [8728] ::ffff:62.114.212.210 TLS: Initial packet from [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2), sid=3f40e2cc ce95cd0e
Sat May 1 01:52:01 2021 us=79334 [8728] ::ffff:62.114.212.210 UDPv6 WRITE [26] to [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ 0 ] pid=0 DATA len=0
Sat May 1 01:52:03 2021 us=159752 [8728] ::ffff:62.114.212.210 UDPv6 WRITE [14] to [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ ] pid=0 DATA len=0
Sat May 1 01:52:04 2021 us=199834 [8728] CID is :5
Sat May 1 01:52:07 2021 us=323761 [8728] ::ffff:62.114.212.210 UDPv6 WRITE [14] to [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ ] pid=0 DATA len=0
Sat May 1 01:52:16 2021 us=31765 [8728] ::ffff:62.114.212.210 UDPv6 WRITE [14] to [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ ] pid=0 DATA len=0
Sat May 1 01:52:19 2021 us=439780 [8728] CID is :5
Sat May 1 01:52:32 2021 us=615821 [8728] ::ffff:62.114.212.210 UDPv6 WRITE [14] to [AF_INET6]::ffff:62.114.212.210:55306 (via ::ffff:197.51.132.181%Port2): P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ ] pid=0 DATA len=0
Sat May 1 01:52:35 2021 us=43754 [8728] CID is :5
and this is picrs of configuration
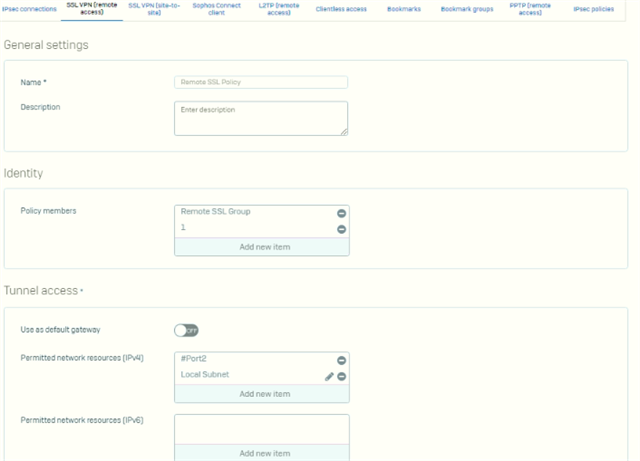
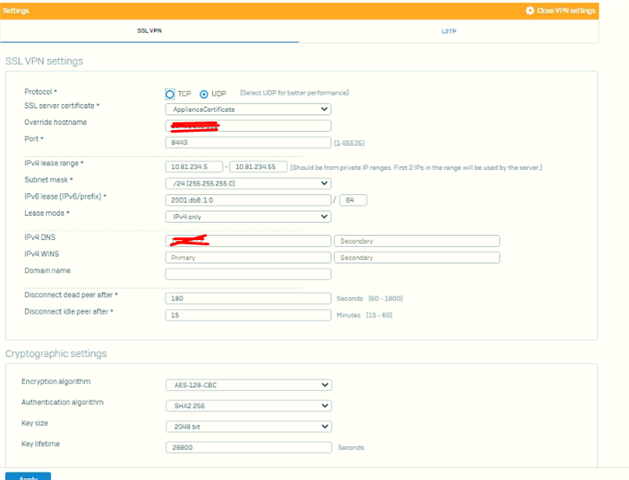
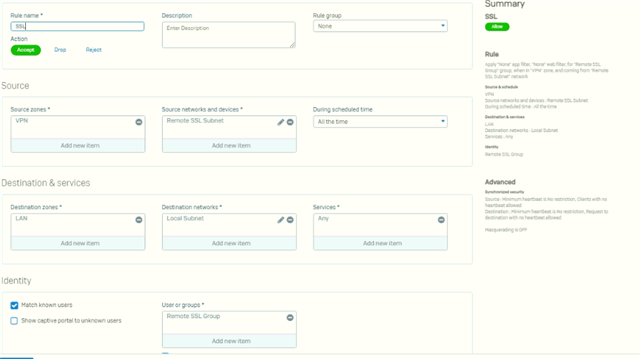
any idea or suggestions about what causing such as this problem ?
thanks in advanced
This thread was automatically locked due to age.


