Hello,
i now switched from a XG105 (17.5.15) to a XG106 (18.0.5).
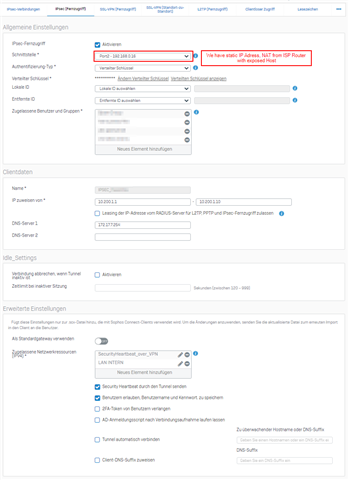
The XG is behind a ISP NAT Device with exposed Host configuration, so Port 4500 and 500 comes trough, i could check that with using the Connect Client on Windows 10.
My Mobile config looks like that:
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>IPSec</key>
<dict>
<key>AuthenticationMethod</key>
<string>SharedSecret</string>
<key>RemoteAddress</key>
<string>IPAdress</string>
<key>SharedSecret</key>
<data>!?EASYKEY!$ #also tried with original long string</data>
<key>XAuthEnabled</key>
<integer>1</integer>
<key>XAuthName</key>
<string>username</string>
</dict>
<key>IPv4</key>
<dict>
<key>OverridePrimary</key>
<integer>0</integer>
</dict>
<key>PayloadDescription</key>
<string>Configures VPN settings, including authentication.</string>
<key>PayloadDisplayName</key>
<string>Sophos IPSEC settings</string>
<key>PayloadIdentifier</key>
<string>com.sophos.iphone.profile.vpn1</string>
<key>PayloadOrganization</key>
<string>Sophos</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadUUID</key>
<string>3D8B5E8B-FARA-3BG1-B451-AA0A9824A0BF</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Proxies</key>
<dict/>
<key>UserDefinedName</key>
<string>IPSEC_Name</string>
<key>VPNType</key>
<string>IPSec</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>Sophos profile for iPhone.</string>
<key>PayloadDisplayName</key>
<string>Sophos profile</string>
<key>PayloadIdentifier</key>
<string>com.sophos.iphone.profile</string>
<key>PayloadOrganization</key>
<string>Sophos</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>C8586117-4FF4-3840-A1D5-52E10AB757BA</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
IPSec-logs:(when trying to connect from Mobile iOS Device):
2021-04-25 10:47:24 27[NET] <14> received packet: from 80.187.102.14[500] to 192.168.0.16[500] (848 bytes) 2021-04-25 10:47:24 27[ENC] <14> parsed ID_PROT request 0 [ SA V V V V V V V V V V V V V V ] 2021-04-25 10:47:24 27[IKE] <14> received NAT-T (RFC 3947) vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-08 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-07 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-06 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-05 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-04 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-03 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-02 vendor ID 2021-04-25 10:47:24 27[IKE] <14> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID 2021-04-25 10:47:24 27[IKE] <14> received XAuth vendor ID 2021-04-25 10:47:24 27[IKE] <14> received Cisco Unity vendor ID 2021-04-25 10:47:24 27[IKE] <14> received FRAGMENTATION vendor ID 2021-04-25 10:47:24 27[IKE] <14> received DPD vendor ID 2021-04-25 10:47:24 27[IKE] <14> 80.187.102.14 is initiating a Main Mode IKE_SA 2021-04-25 10:47:24 27[ENC] <14> generating ID_PROT response 0 [ SA V V V V V ] 2021-04-25 10:47:24 27[NET] <14> sending packet: from 192.168.0.16[500] to 80.187.102.14[500] (180 bytes) 2021-04-25 10:47:24 07[NET] <14> received packet: from 80.187.102.14[500] to 192.168.0.16[500] (380 bytes) 2021-04-25 10:47:24 07[ENC] <14> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ] 2021-04-25 10:47:24 07[IKE] <14> local host is behind NAT, sending keep alives 2021-04-25 10:47:24 07[IKE] <14> remote host is behind NAT 2021-04-25 10:47:24 07[ENC] <14> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 2021-04-25 10:47:24 07[NET] <14> sending packet: from 192.168.0.16[500] to 80.187.102.14[500] (396 bytes) 2021-04-25 10:47:25 12[NET] <14> received packet: from 80.187.102.14[3608] to 192.168.0.16[4500] (108 bytes) 2021-04-25 10:47:25 12[ENC] <14> invalid ID_V1 payload length, decryption failed? 2021-04-25 10:47:25 12[ENC] <14> could not decrypt payloads 2021-04-25 10:47:25 12[IKE] <14> message parsing failed 2021-04-25 10:47:25 12[ENC] <14> generating INFORMATIONAL_V1 request 1878755533[ HASH N(PLD_MAL) ] 2021-04-25 10:47:25 12[NET] <14> sending packet: from 192.168.0.16[500] to 80.187.102.14[500] (92 bytes) 2021-04-25 10:47:25 12[IKE] <14> ID_PROT request with message ID 0 processing failed 2021-04-25 10:47:25 12[DMN] <14> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from 80.187.102.14[3608] failed 2021-04-25 10:47:28 28[NET] <14> received packet: from 80.187.102.14[3608] to 192.168.0.16[4500] (108 bytes) 2021-04-25 10:47:28 28[ENC] <14> invalid ID_V1 payload length, decryption failed? 2021-04-25 10:47:28 28[ENC] <14> could not decrypt payloads 2021-04-25 10:47:28 28[IKE] <14> message parsing failed
Hope you have some suggestions.
Regards
This thread was automatically locked due to age.