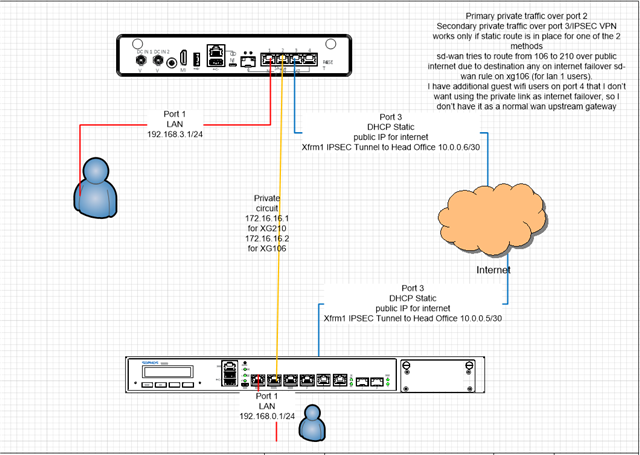
I have an XG210 and an XG106.
They are connected by a private circuit on port 2 of each device, and traffic has existing static routes on each to use that to reach private subnets at each end, etc.
We are now turning up IPSEC VPN between them, using the standard ike 2. The vpn itself connects fine and the xfrm interfaces can ping each other ok.
For the remote site, I have one public internet connection from a cable provider (which is the only link under WAN manager).
The upstream private circuit also does have the capability of being internet access through the head office XG210 as well.
Because the private circuit is "LAN" type (with nat and additional filtering upstream), it is not in the wan manager as a default gateway, which is ok.
If I have 1 SD-WAN rule for destination any, using cable internet as primary and the private circuit as backup, it fails over and back properly.
If I try and build my additional SD-WAN rule where i want to just reach certain private networks via the private circuit as primary, and the new VPN secondary, it never works as the destination ANY SD-WAN rule overrides it, even though the private network rule has a more specific destination address.
I've also set it to the top rule in the sd-wan page and it still doesn't take effect.
I see this in the documentation and it simply says to make sure static routing is first, sd-wan second, and vpn routes third.
I don't have any static routes as I have removed the static routes (which work) for sd-wan to allow failover between private circuit and the VPN as backup.
How do I get the private subnets to use the sd-wan rule without totally removing my destination any default sd-wan policy which is doing my internet traffic?
Otherwise I will have to redo my private LAN as a WAN and make new firewall rules to limit traffic as only certain users can use the internet on the private circuit, i don't want it becoming the active link as backup for internet and all users having access upstream to it.
Thoughts?
How do you get more specific sd-wan routes to work without the destination any sd-wan rule overriding everything?
This is easily done on cisco, juniper, etc...
This thread was automatically locked due to age.