I Have a Site A (remote) using an PfSese firewall with several Vlans.... The Central Site is also using a PfSense as Firewall ...every site have several VLANS both with IP Public.
The VPN is already working but they need to replace the PfSense at remote site for a XG Firewall in order to connect with the Pfsense in Central site.
Both sites have Public IP address and use a PPPoE connection from a Internet provider with a vlan in the WAN port with a vlan ID ...
The image shows the remote site configuration (working) and we wanna replace this PfSense with a XG Firewall (you can see there are several Vlans from REmote Sites connected to Central Site
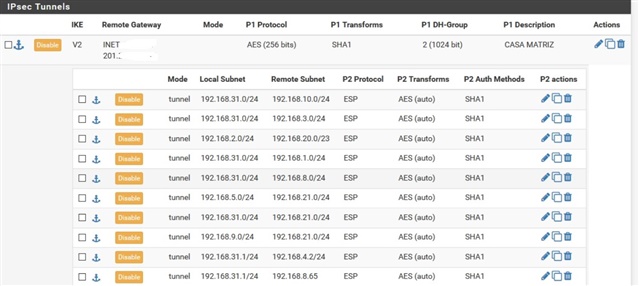
Trying to connect a VLAN from A (192.168.31x) to several Vlans from B (192.168.10.x, 192.168.20.x 192.168.3.x)as the picture above in one IPsec connection with one IPsec Policy i just can connect one VLAN from A to one VLAN from B
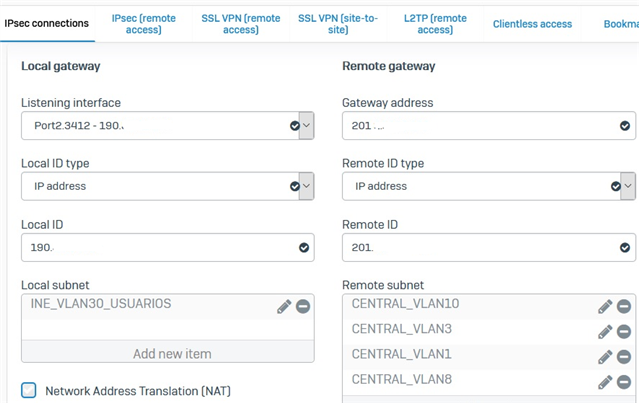
In site A I declare the VLAN needed from site A remote (XG firewall ) to connect to the Vlans in site B Central (Pfsense). I also include the Firewall rules to in and out the traffic to the Central site
The configurarion is as follow
The XG Firewall connect to the remote site Pfsense and the result show only one connection
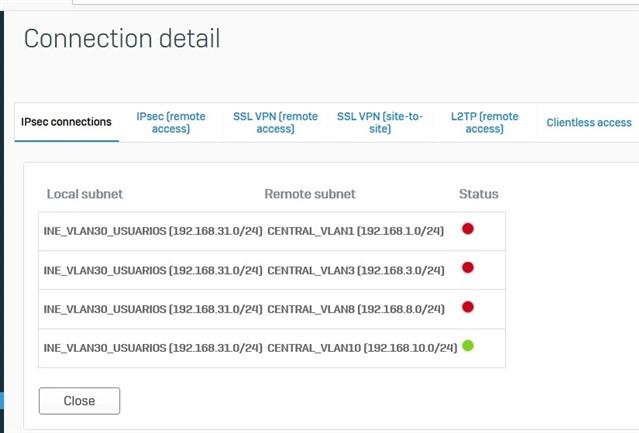
I already try several ways to connects multiple vlans between Xg Firewall and another XG Firewall on a Laboratory using the same configuration and i have no problems also with more Vlans at both sides
The PfSense use several Vlans as remote and local and as I mentioned the VPN is already working and the need to user one XG firewall at the remote site ...
Since the one VLAN from remote site (XG Firewaal) is connected to the a Vlan in central Site .... i supposed the configuration for IP's F1 and F2 and PSK are corect but i can't get all vlans connected ...
Where can the be the error ??
This thread was automatically locked due to age.


