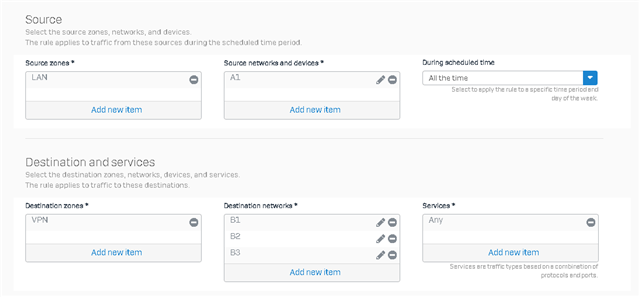
I have site A with the follow Vlans A1 A2 A3 A4 A5, Site B with the follow Vlans B1 B2 B3 B4 B5
If I configure one VPN between A and B with all Vlans included, i will have a total of 15 conections (5+4+3+2+1).. all A1 to A5 to B1 to B5 posible conections .
I just need to stablish a VPN (IPsec) site to site o Routed Base VPN or SSL VPN site to site as follow
A1 with B1 B2 B3
A2 with B2 B5
A3 with B3
A4 with B4
A5 with B4 B5
In total just need 9 conections some of them like A4 just visible to B4
Wich way or how i must configure each side ??
Thanks for your help
This thread was automatically locked due to age.