Hallo,
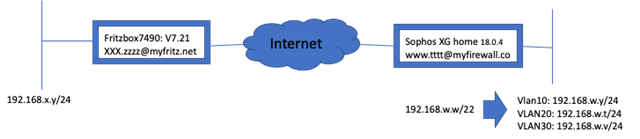
urgent help for VPN- Site to site connection between a fritzbox 7490 V7.21 and Sophos XG home V18.0.4. I cannot establish the VPN.
A short overview:
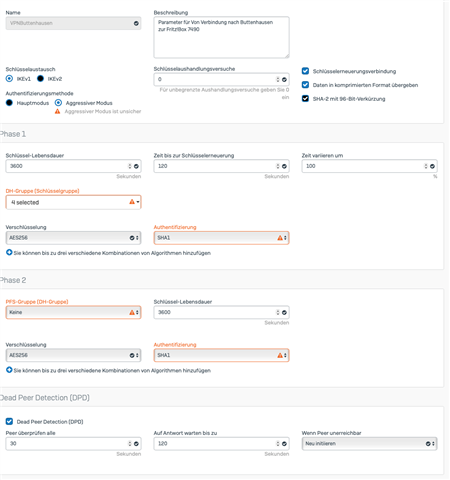
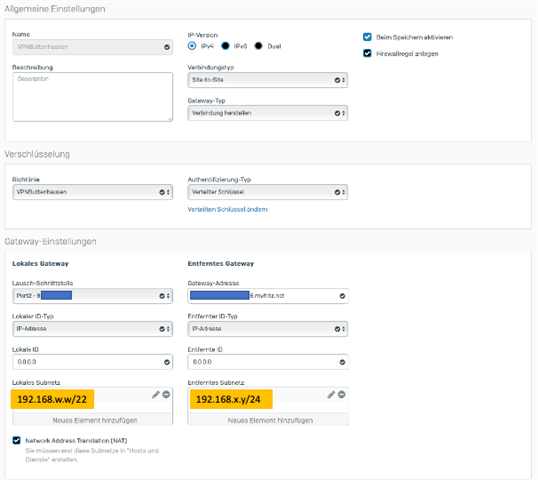
Config file of the Fritzbox:
enabled = yes;
editable = yes;
conn_type = conntype_out;
name = "Buttenhausen Plochingen";
boxuser_id = 0;
always_renew = no;
reject_not_encrypted = no;
dont_filter_netbios = no;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remoteip = 0.0.0.0;
remote_virtualip = 0.0.0.0;
remotehostname = "fw-greiner-pl01.myfirewall.co";
keepalive_ip = 192.168.0.1;
localid {
key_id = "$$$$3RIQ4SWQN4QTNDLGZMTISOESJ1VNTVMFUBRMRBYQD35ZPTL4CKMITRQKGV4LN33KD3ZMX5XYT6FHYAAA";
}
mode = phase1_mode_aggressive;
phase1ss = "all/all/all";
keytype = connkeytype_pre_shared;
key = "$$$$B4XPAPG6TY2MBP2A3NJPXELFK3AIR14URHLGOPM5EPTZJE23OZ1EENATV5EPKEOTYGUO6SYNL5BWUAAA";
cert_do_server_auth = no;
use_nat_t = yes;
use_xauth = no;
use_cfgmode = yes;
phase2localid {
ipnet {
ipaddr = 0.0.0.0;
mask = 0.0.0.0;
}
}
phase2remoteid {
ipnet {
ipaddr = 0.0.0.0;
mask = 0.0.0.0;
}
}
phase2ss = "esp-all-all/ah-none/comp-all/no-pfs";
accesslist = "permit ip any 192.168.w.w 255.255.252.0"
app_id = 0;
This thread was automatically locked due to age.


