Hello,
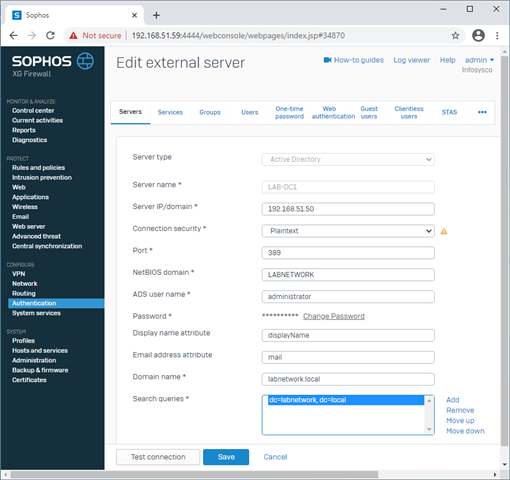
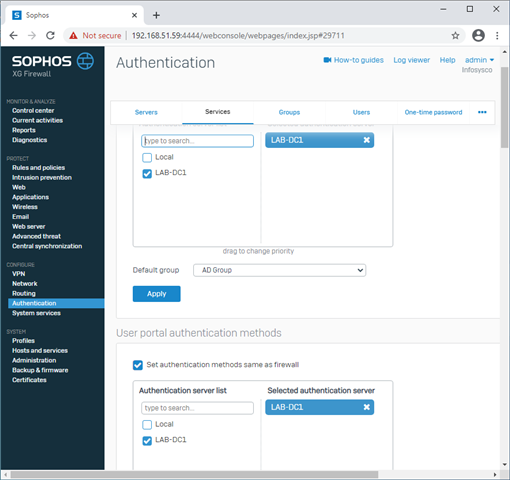
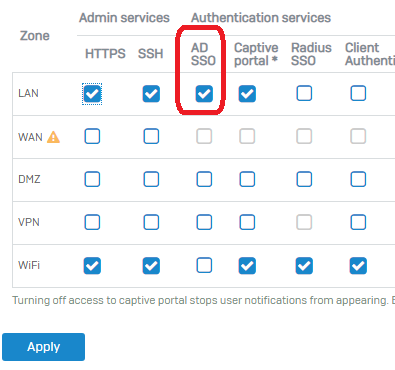
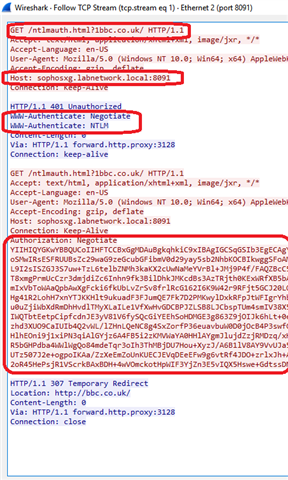
I am looking for the most efficient way to handle users in an AD environment where non AD users exists (from personal computers or phones or other devices that need special treatment).
Suppose I have a rule to filter traffic from known users (either with STAS or with AD groups), how to handle traffic for those non known users? Using a rule above the known users rule?
Best regards
K
This thread was automatically locked due to age.