We have recently setup a new XG running OS 18.0.4.
We have remote client using Sophos Connect.
We also have an Azure based web server, off site (obviously) that is locked for FTP access ONLY to our office WAN IP.
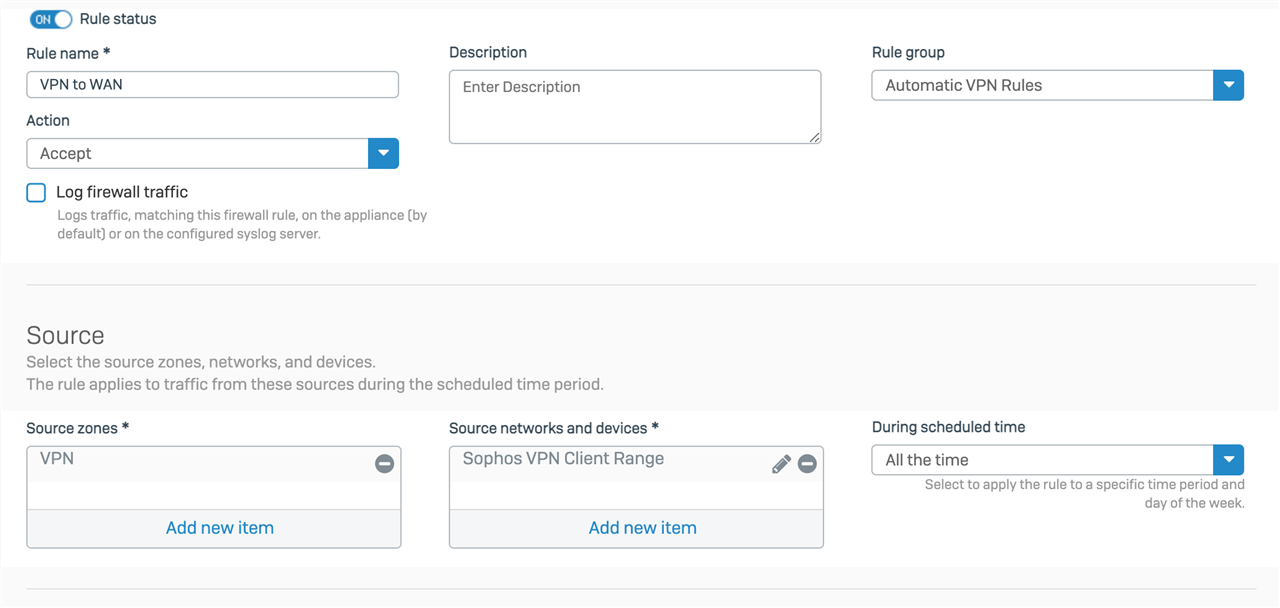
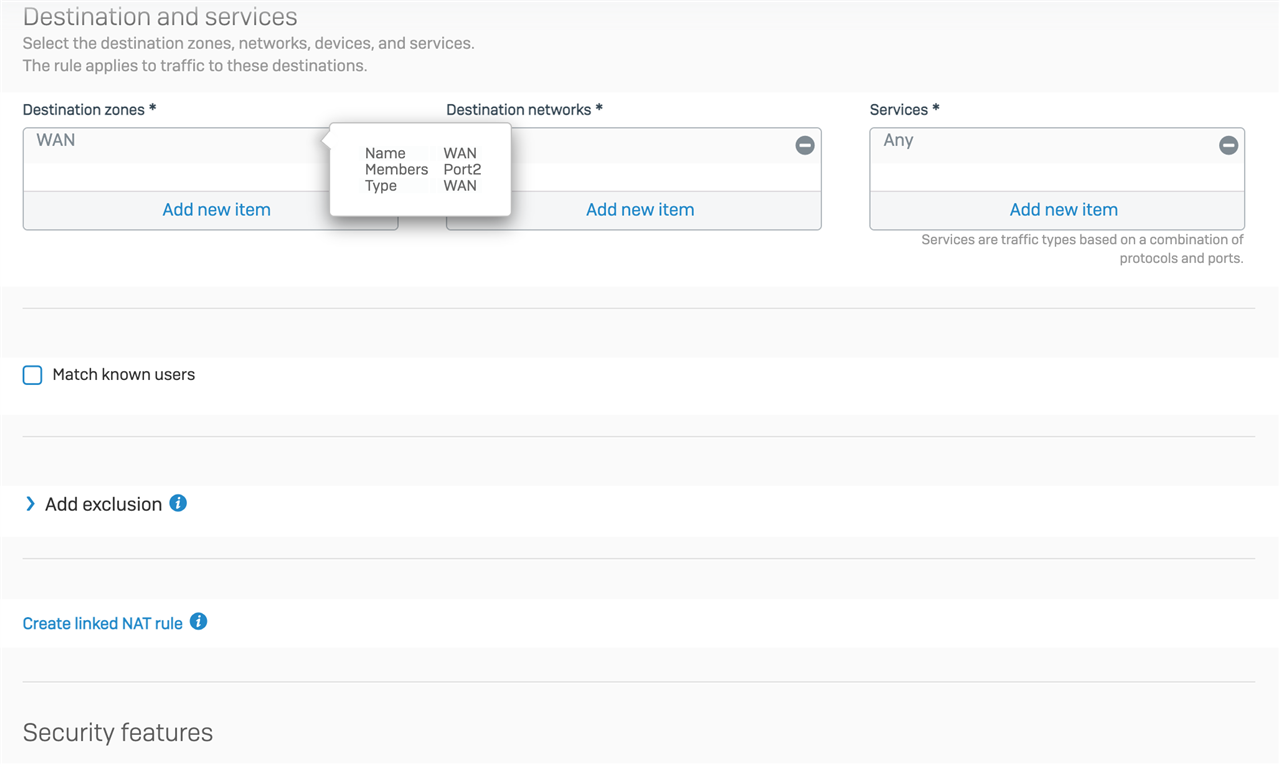
From the office, no outgoing ports are blocked, and the VPN zone is allow all port access to remote servers.
Now if I run a Passive FTP connection through the VPN to the Azure server, I get Firewall errors of Invalid Traffic - Denied from a random port usually to port 21, or from 21 to the WAN IP. In addition, the file transfers often fail, but not all the time, as in if I upload a folder of items, some make it through and some error.
But if I do the same task from a machine sat in the office, it seems to copy ok, although it does seem to hit errors in the firewall log still.
On our old Sonicwall we had no issues doing the same tasks.
Any ideas?
This thread was automatically locked due to age.