Hello All. I hope everyone is having a good weekend.
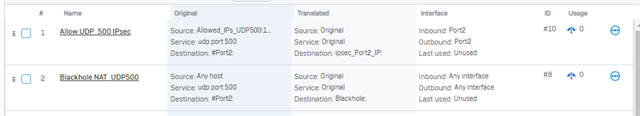
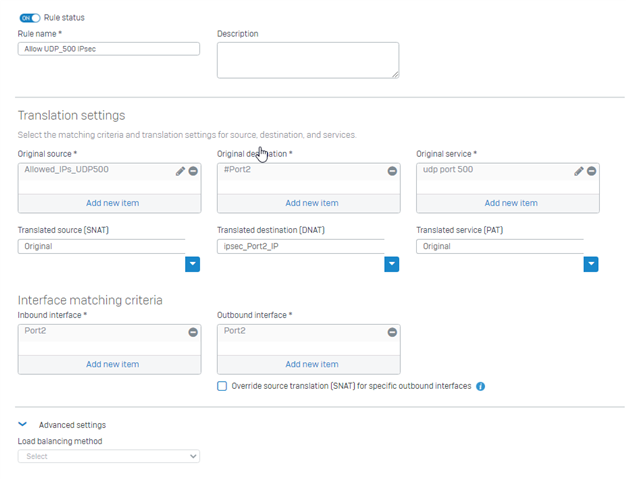
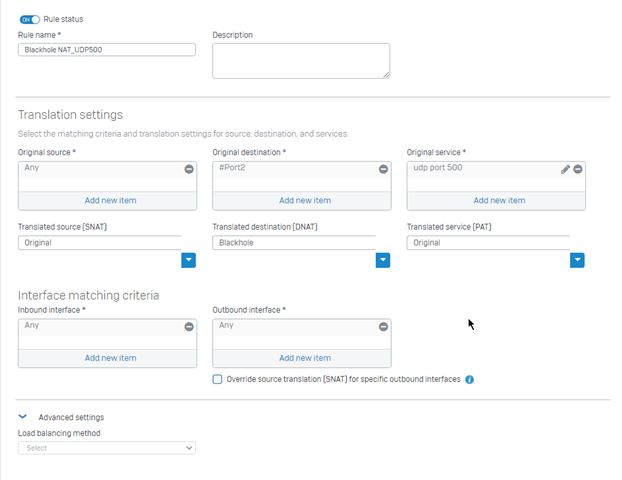
So we are replacing about 62 older Sophos UTM 9.0's with Sophos XG's. All of these sites are have been connected for years with a hub and spoke VPN via site to site IPSec VPN tunnels and we have never had an issue passing PCI scans. However we have deployed 12 of the 62 XG's and each one of those fails with UDP port 500 open. We have looked at the solutions provided such as disabling strongswan or sending UDP500 to a blackhole (preferred). These get the XG's to pass the scan but UDP500 is needed for IPSec site to site tunnels and they fail. These devices have nothing enabled on the WAN ports under Device Access that would cause this.
Other than disputing it with the PCI Scan Vendor (Trustwave) how have you handled this situation.?
What is odd to me is that all the existing UTM's are working fine (They can initiate as well as respond to IPSec). When I do a nmap scan against the IP address on UDP port 500 it shows as Open/Filtered on the UTM's but Open on the XG's which is likely why it is failing.
Others have suggested limited UDP500 via peer IP's and I can easily do that since all sites are static. However, I do not think it is possible to limit this via a firewall rule.
Thanks everyone for any ideas.
Dave
This thread was automatically locked due to age.