Hello everyone...
I've been looking for my problems resolution for more than a week but haven't found similar situation.
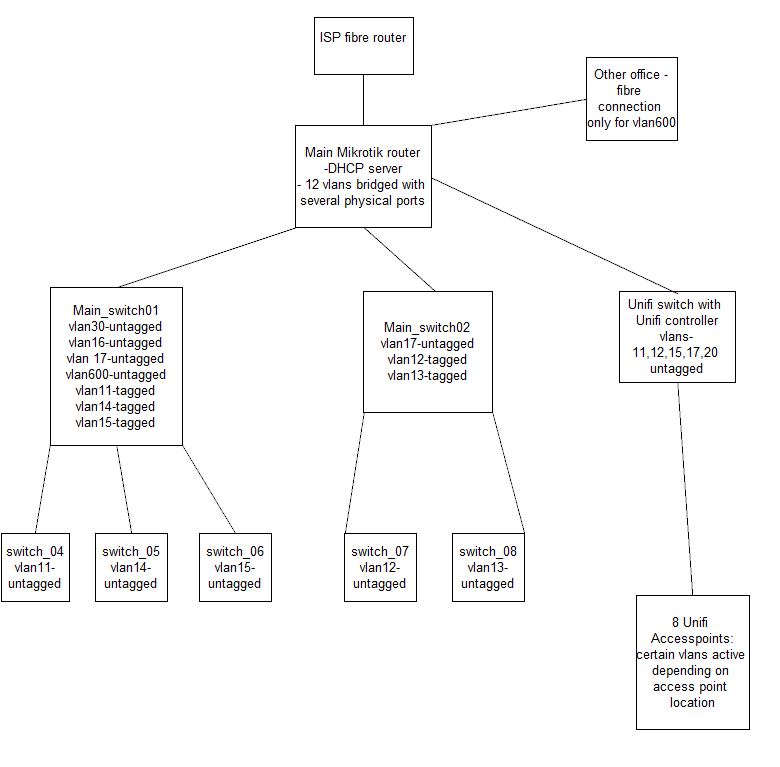
I'm a new user of XG 310 with 18.0.4 firmware. I want to replace Mikrotik router which is the main part of the network with the new XG 310. New device should serve as router and firewall.
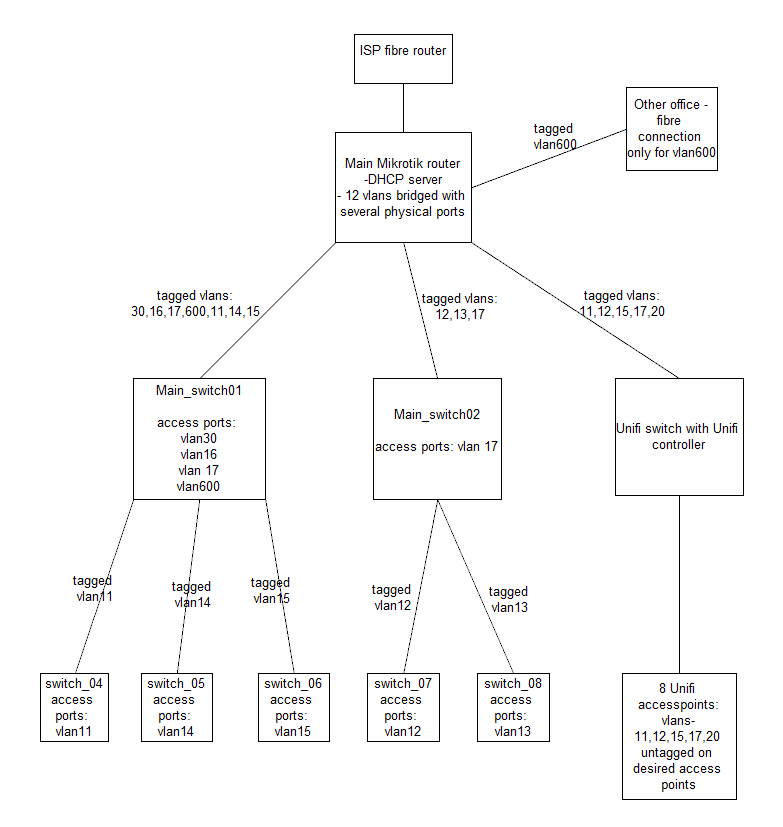
So, at the moment we have Mikrotik router connected to ISP modem. There are 12 vlans created on the router's main bridge. All vlans are sent from router to two main Mikrotik switches and Ubiquiti switch. There are several access points connected to the last switch. Vlans are passed from main switches to 5 more switches.
I'm trying to get similar or any working configuration in the test environment. I need two 'trunk' ports to connect main_switch1 , main_switch2 and propagate all created vlans. I created a bridge with IP addresss, added ports 5 and 6 on Sophos, created vlan30 and added them to the bridge. Routing and vlan filtering are enabled on the bridge. Vlan30 is chosen within the filtering option on bridge.
I also created DHCP server for my vlan. I connected port 5 of xg310 to configured trunk port on DCN S4600. I made rule : allow traffic from network 10.10.0.0 (vlan30), to WAN . I also linked NAT MASQ to it.
When I connect my laptop to untagged port of DCN I get IP address ,DNS from Sophos. The issue is: I can always ping WAN devices but when I try to reach websites they are sometimes accessible and sometimes they are not. Log viewer showed me that traffic from laptop's IP either goes through bridge.30 interface or port 5. Second case is unwanted and because there's no rule about port 5, traffic is rejected.
How can I solve this issue?
Is there a better, simpler and/or more effective way of replacing main Mikrotik router with XG firewall in this scenario ?
This thread was automatically locked due to age.