Hello everyone,
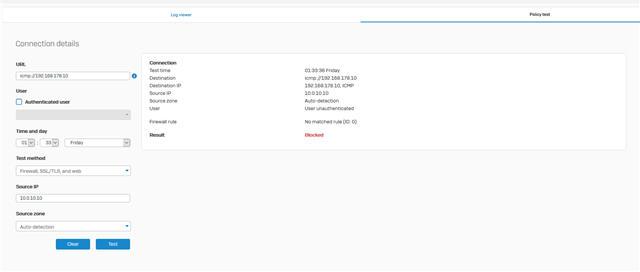
I have a VLAN 10 which is my DMZ and I want to disable/block access to my internal Network (VLAN 1).
I can ping every Device from my DMZ and access every LAN-Device.
I already tried to add a BLOCK Rule, but my Sophos seems to ignore it.
Anybody got an Idea how to block these?
This thread was automatically locked due to age.