I apologize if this has been explained somewhere else and please feel free to direct me to the answer.
I have a XG appliance that we want to bridge 2 interfaces and create them as a bridged trunk for VLANs.
So on the XG we have int 1 and int 2 that will each be connected to 2 different switches (not switch stacked). Each of these switches need to have the same VLANs associated to them.
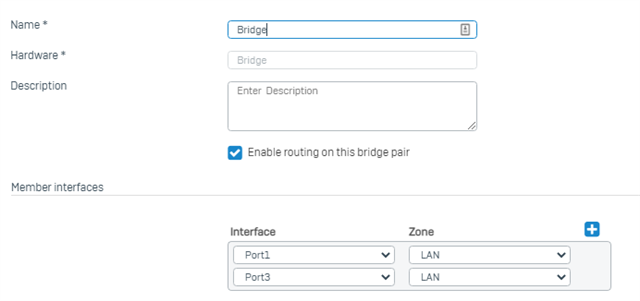
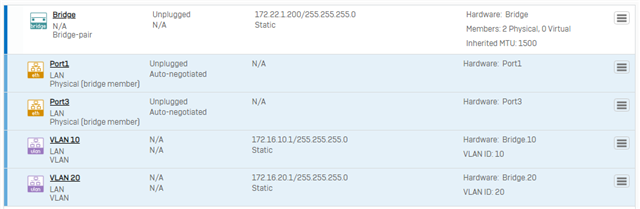
I have created a IPed bridge by adding interface 1 and interface 2 and assigning a interface IP to it. I then added VLAN 10 and VLAN 20 as sub interfaces on said bridge.
Problem I have is that devices connected at the end on either VLAN 10 or VLAN 20 cannot communicate to anything.
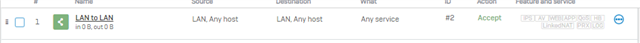
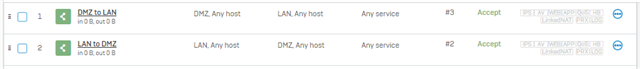
I have read that I might have to create rules to allow the traffic to pass from the sub interface VLAN 10 to any other zone.
Can someone give a more detail explanation or example of this to help me fix up my issue?
This thread was automatically locked due to age.