Hello to all!
Since a few days I am evaluating XG in order to replace my UTM
I have been running Sophos UTM for the last 5+ years, have been extremely pleased with it, but I started considering to move on.
So installed XG on a second machine I have...
I find XG's logic more... logical to be honest, but this does not mean that I can necessarily follow this logic, especially for someone like me who has been spoiled for so many years with the UTM's user friendliness.
Anyway, my use case is the below:
One WAN connection using PPPoE with a 3G failover. (I will soon be adding a second WAN connection via a WISP, but that is a matter for another day)
I have a few NAT rules to access some non important services remotely. I use VPN to access securely my important stuff
I have a couple of VLANs for guests and IoT devices.
I also have 3 dynamic dns hostnames that point to 3 different machines on my internal network.
I use Advanced threat protection, web filtering and application control in order to block ads and access to bad sites (aka young kids)
Also a few web filtering profiles to block internet access using some criteria (e.g. kids tablets during specific hours, IP cameras etc)
So I started my tests to see how I can transfer my configuration to XG. Not a dead easy task, XG wan port is now connected to the guest network, so cannot simulate my PPPoE WAN and have this as DHCP. I assume PPPoE will have no issues, though, will just need to change the interface type when I decide to go in production.
I also checked NAT options. After a quick look I realized that while on the UTM I was creating 2 rules (DNAT and Full NAT) in order to access from inside using the "external" address, now on XG it is only a checkbox to enable this option. Really nice (unless I was stupid with my UTM config and dual rules were not needed, that is)
VLANs also are straight forward on XG, as I see, and the usage of Zones makes things much more organized IMHO.
The log is another thing... Pardon me, but the one on the UTM was not good. Especially since there were essentially no filtering options, trying to find something using the available method was simply a pain. In XG things appear to be much easier in this regard. Of course I will clearly find out when I go live with XG, because in my test environment I have for starters only one machine behind XG, so not the same thing
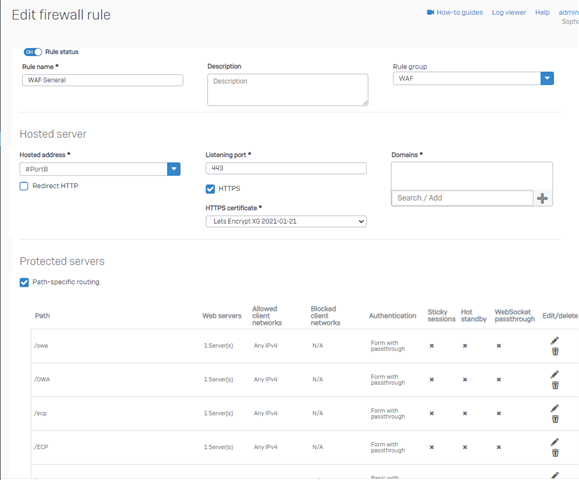
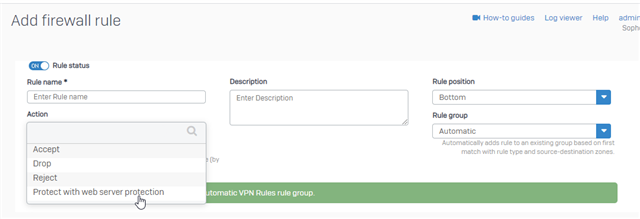
I then went on to the DynDNS thing. I am accustomed to the UTM logic where I was adding the dynamic dns account, then on webserver protection creating real webservers, then the virtual ones and was assigning the dyndns host to the virtual webserver.
I did not see the same approach on the XG... how does this work in XG? Not entirely clear to me, granted I only played a few hours with it, so will have to explore more I guess. Searching about this, however, I realized that everything I could find was about the new feature where sophos can be used as a DDNS server. (BTW does this mean I can discard what I have now and use sophos for 3 or more hostnames that I need?)
An important question: Is something important still missing from XG compared to UTM features? (I remember in the past reading posts about some missing features that were deal breakers for some users. But I can't find those any more and additionally XG has evolved a lot since then and said features may be already added by now)
A thing that it is missing and it bothers me is the lack of UPS management. Having this I know it is not extremely important in a firewall and UTMs implementation was pretty basic anyway. Nevertheless, the ability to gracefully shutdown the machine was nice to have. Additionally, the notifications of a power loss via email was a good piece of information. I liked that even when I was away I was still aware of power issues at my house. Do you think it will ever be added to XG? I hope so, even at the basic form UTM had it.
Another thing... The test machine I have now is using a Haswell core i3-4130 CPU with 8GB of RAM ( I know 6 is only used in Home edition). So it is powerful enough. My actual firewall has an Atom C2358 with 4 GB of RAM (it can be upgraded to more RAM if needed). Do you thing it can handle XG with the same stuff running in the background as UTM does?
Is there anything else I should be aware of before I make the transition, or after my transition?
Thanks in advance for all your comments/answers!!
This thread was automatically locked due to age.