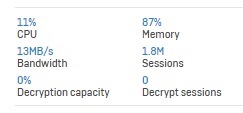
We have an XG 550 rev. 2 configured with 2 different internet connections and a 10 gig fiber card for the LAN port. We have been experiencing DDOS attacks which we have an external service mitigating. What we have found is that at certain times during the attacks or even after they have subsided we experience the XG getting extremely high session counts (1.5 million, 1.8 million, even 2.1 million at one point). This causes our internet connectivity to grind to a halt for some amount of time. The slowness is unusable in most cases.
Sometimes we disconnect the ISP line that doesn't have DDOS mitigation on it to see if we can fix the issue. It almost feels like when we do that, the session count and memory usage climbs through the roof. In one case we had the second line disconnected, the attack was mitigated on the first line, but the session count and memory stayed high. We rebooted the firewall, down for 10 minutes then the sessions went right back up! We plugged the second line back in and immediately the session count came down. So confused. Can anyone shed any light on this?
This thread was automatically locked due to age.

