Hello,
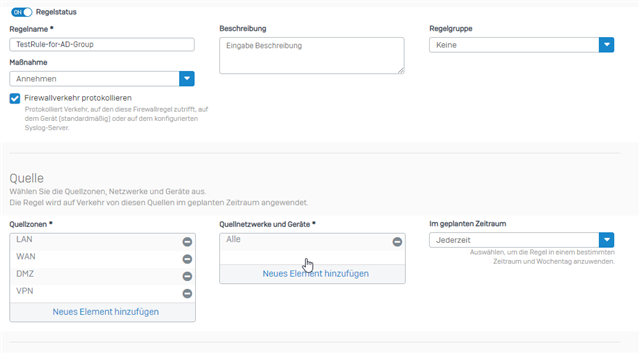
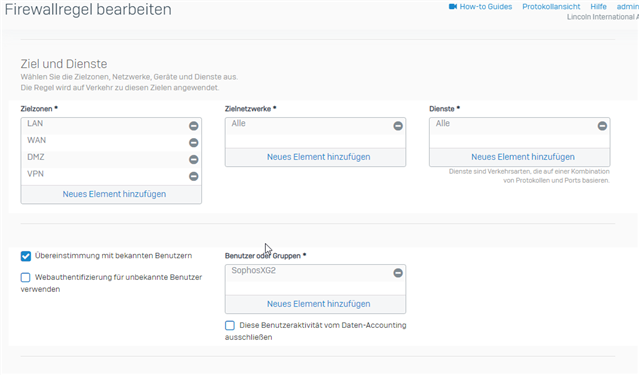
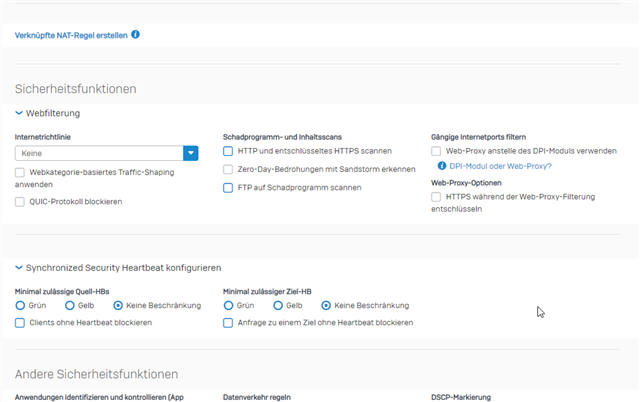
we are facing this issue from the beginning (pre MR4) and have an open case on it for 3 month which seems stuck. So i´m trying it with a forum post. The XG is a standalone System XG230 (SFOS 18.0.4 MR-4). We have disabled all related features and still we get certificate warnings with signed Sophos SSL CA. This behaviour can be seen in the browser as well as applications like outlook and zoom. Here is the relevant configuration:
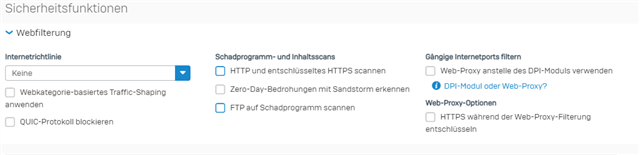
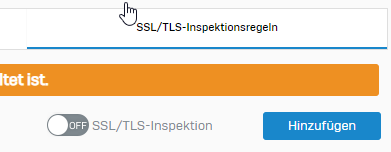
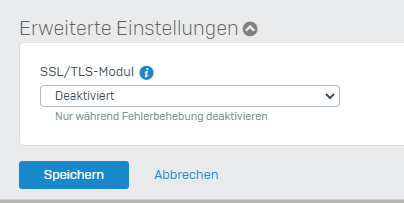
Application control is deactivated aswell. Only thing in place is User Authentication via Synchronized User ID and Heartbeat enforcement:
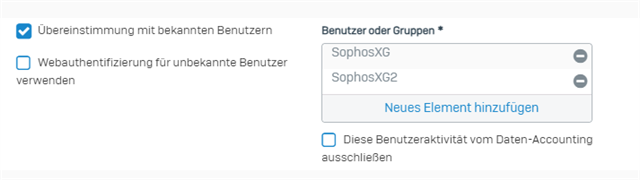
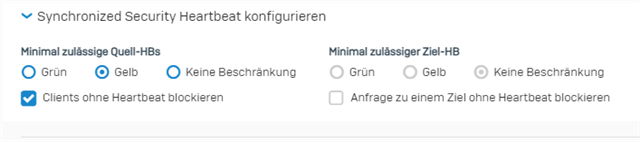
Web Filter log shows denied messages for seemingly no reason:
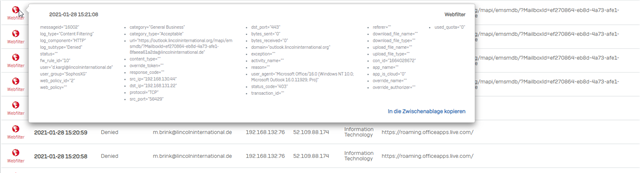
The machting FW rule is the one descriped above. Im wondering that there are even messages in the Webfilter Log since its disabled.
SSL/TLS-Inspection Log is empty.
Any Ideas would be much appreciated!
This thread was automatically locked due to age.