Okay, I have something strange that I don't seem to get.
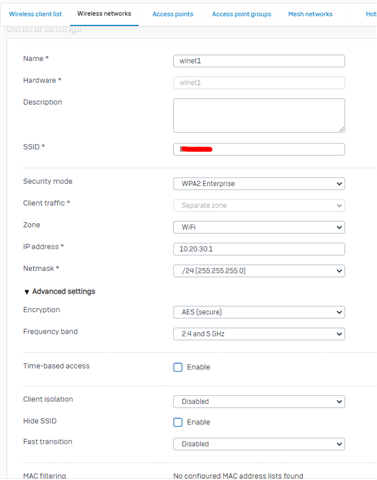
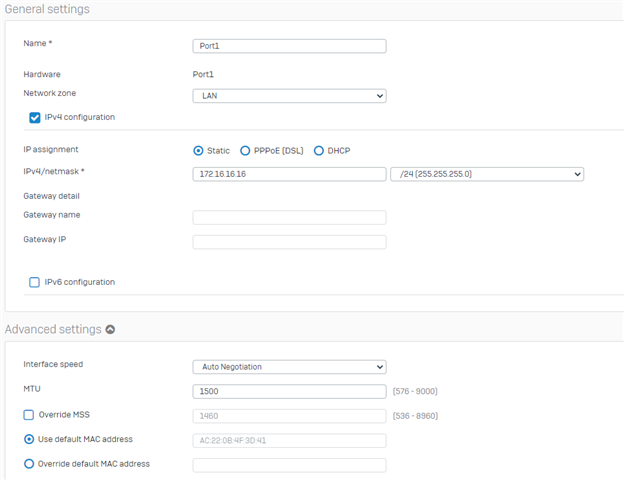
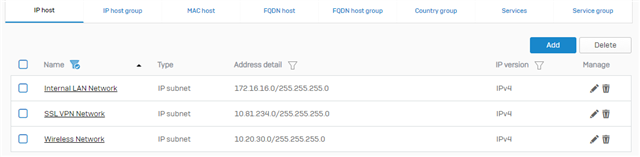
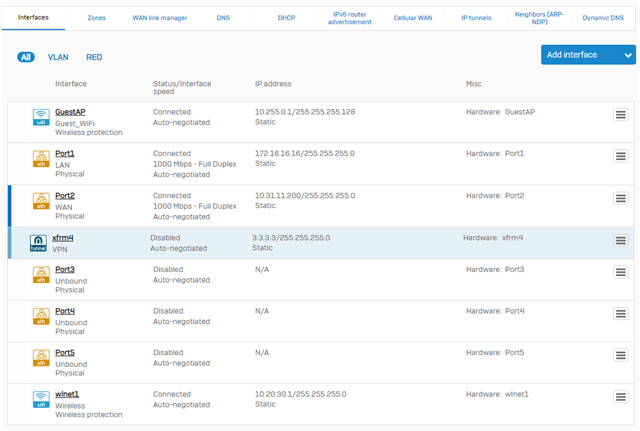
I have my normal LAN zone with my Internal Network range. In this zone I have an AP55C access point and the access point in turn has a Wireless network in a separate zone (called WiFi).
I needed to enable traffic from LAN to WiFi zone, so I created a firewall rule:
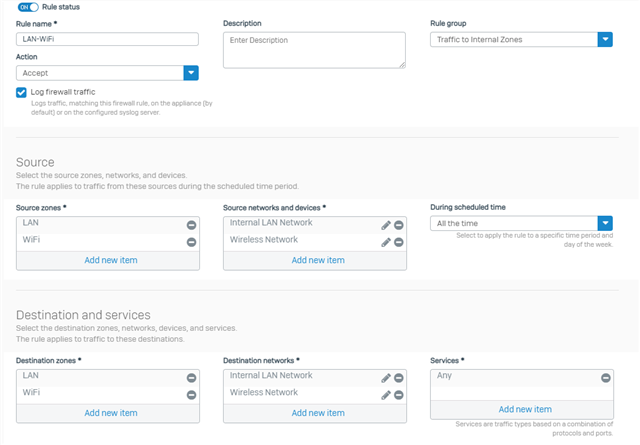
However, no traffic is hitting this rule. I have checked and double checked zones and networks.
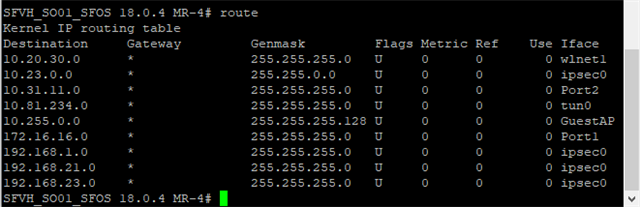
The LAN zone can ping the Firewall address of the WiFi zone. Wifi zone can browse the internet through the XG and all hosts have the XG as their default gateway.
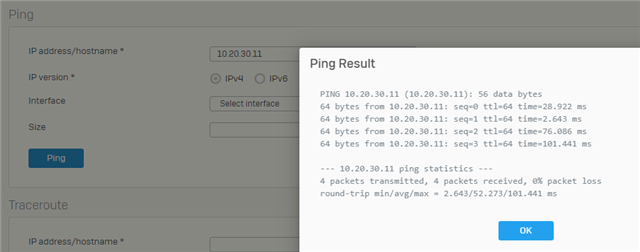
In a packet trace from I see the following information coming back over and over, I try to telnet from the LAN zone client to the WiFi zone client on port 4747 since a service is listening there.
|
2021-01-07 11:28:40
|
Port1
|
wlnet1
|
IPv4
|
172.16.16.100
|
10.20.30.11
|
TCP
|
54231,4747
|
0
|
0
|
Violation
|
Firewall
|
No policy
|
No policy
|
SYN_SENT
|
|
2021-01-07 11:28:40
|
Port1
|
IPv4
|
172.16.16.100
|
10.20.30.11
|
TCP
|
54231,4747
|
0
|
0
|
Incoming
|
No policy
|
No policy
|
NONE
|
There is always 0B in and 0B out on this firewall rule.
I have changed the rule to explicitly allow from LAN any to Wifi any but it doesn't make a difference. Only when I change the rule to Destination any/any then I start to see the byte count increase (because the rule is high in the chain it then captures all internet traffic from WAN), however still the same packet trace with Violation and not possible to send any traffic from LAN to WiFi zone.
Am I overseeing something, or do I need to make some routing changes in the advanced shell for this to work?
This thread was automatically locked due to age.