Hi all,
Running SFOS 18.0.4 MR-4, and tried to AD join my XG as this was working before but did not use it for a long time.
i have been with this for 4 hours now, but no luck.
Seeing this in the log:
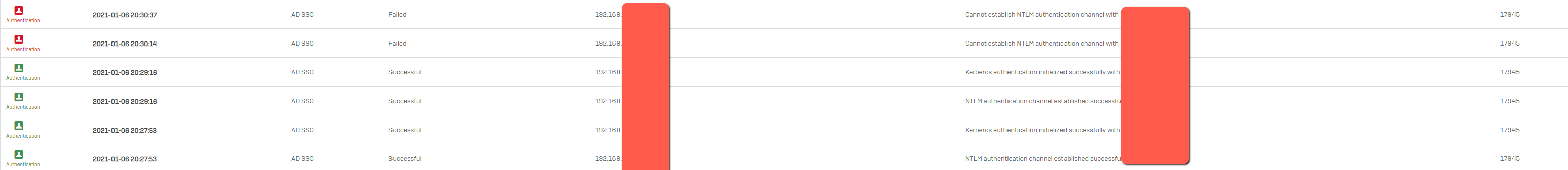
Jan 06 20:32:06.896985 [nasm] executing '/oss/winbindd'
winbindd version 4.7.4 started.
Copyright Andrew Tridgell and the Samba Team 1992-2017
initialize_winbindd_cache: clearing cache and re-creating with version number 2
STATUS=daemon 'winbindd' finished starting up and ready to serve connections
dos charset 'CP850' unavailable - using ASCII
Jan 06 20:32:07.897022 [nasm] is_ad_server_alive
Jan 06 20:32:07.897080 [nasm] is_ad_server_alive: winbindd running fine (this is what system thinks !!)
Jan 06 20:32:07.897101 [nasm] throw_request: written 2096 bytes on winbind pipe
Jan 06 20:32:07.897107 [nasm] catch_response
Jan 06 20:32:07.897111 [nasm] __read
Jan 06 20:32:08.315381 [nasm] we've 3496 bytes on winbindd pipe
Jan 06 20:32:08.315400 [nasm] received response (3496 bytes) from winbindd
Jan 06 20:32:08.315404 [nasm] catch_response
Jan 06 20:32:08.315408 [nasm] NT_STATUS_ACCESS_DENIED: {Access Denied} A process has requested access to an object but has not been granted those access rights. (0xc0000022)
Jan 06 20:32:08.315412 [nasm] is_ad_server_alive: validate_credentials failed
Jan 06 20:32:08.316271 [nasm] pre_channel (done)
Jan 06 20:32:08.316302 [nasm] throwing logs on garner
Jan 06 20:32:08.316326 [nasm] all servers traversed, but still not able to setup channel, will try again in 20 seconds
Jan 06 20:32:08.316345 [nasm] setup_channel (done)
Jan 06 20:32:08.316349 [nasm] waiting for an event on PROTOCOL fd [up to 20s]
Jan 06 20:32:15.013686 [ntlmserver] ntlm_server() ---> epoll_wait() waiting 10s for events
^C
have rejoined the XG to my AD several times, deleted the AD Computer object every time.
Also did this:
Stop the NASM service: service nasm:stop -ds nosync
Remove file /content/nasm: rm -rf /content/nasm
Start the NASM service: service nasm:start -ds nosync
Tried all of this:
NTLM and Kerberos troubleshooting (sophos.com)
Still no joy.
My domain level is 2016 and AD servers are Win 2019
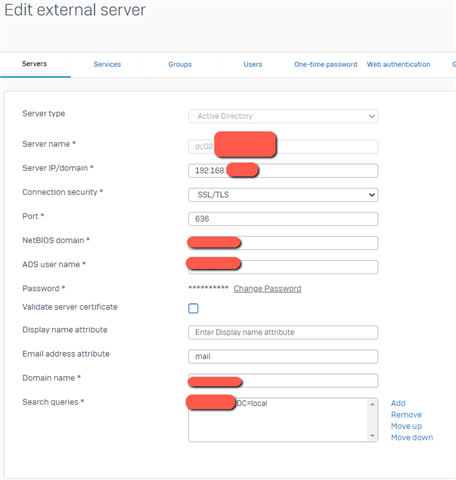
When I press TEST is goes all green and I can import users from AD.
What the h... am I doing wrong?
Also tried with Plain text LDAP, same result.
This thread was automatically locked due to age.

