I have found a couple of old thread about this but cannot find how to do this. Even watched the video from the link in V18 but that didn't help me a lot either.
What I want to achieve is the following:
Traffic from 10.242.12.0/24 (SSL VPN client pool) connecting to 10.23.1.0/24 (VPN IPSEC site-to-site) network should be sourcenatted with 192.168.21.0/24 (Internal network of XG).
I have tried the following with a Linked NAT Rule from a firewall rule:
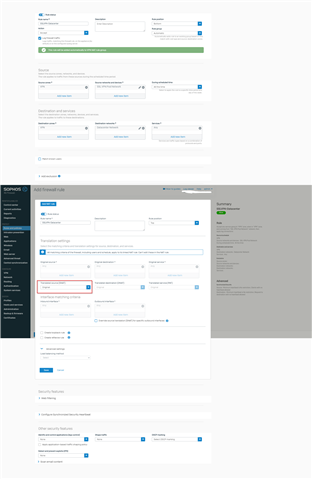
As far as my knowledge goes I should make a network object under Tranlsated Source with 192.168.21.0/24. Creating of the network object works without hassle, but the only objects that are to be found are hostobjects. Seems network objects are not possible to pick.
Then I tried to create just the NAT rule from NAT rules like this:
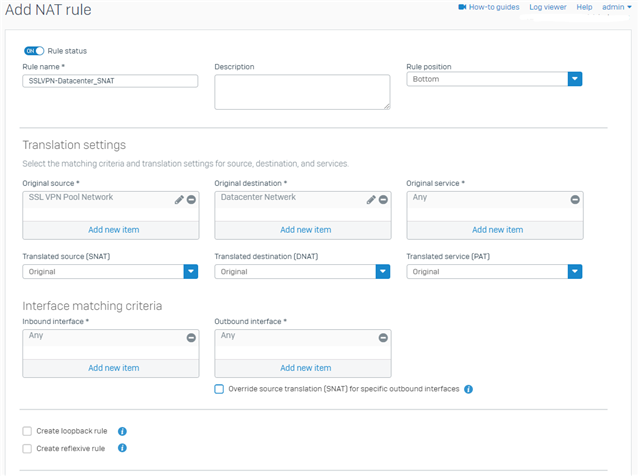
But here the same problem arises that I cannot add a network object to the Translated Source.
How can I make the 1-1 SNAT work?
This thread was automatically locked due to age.
