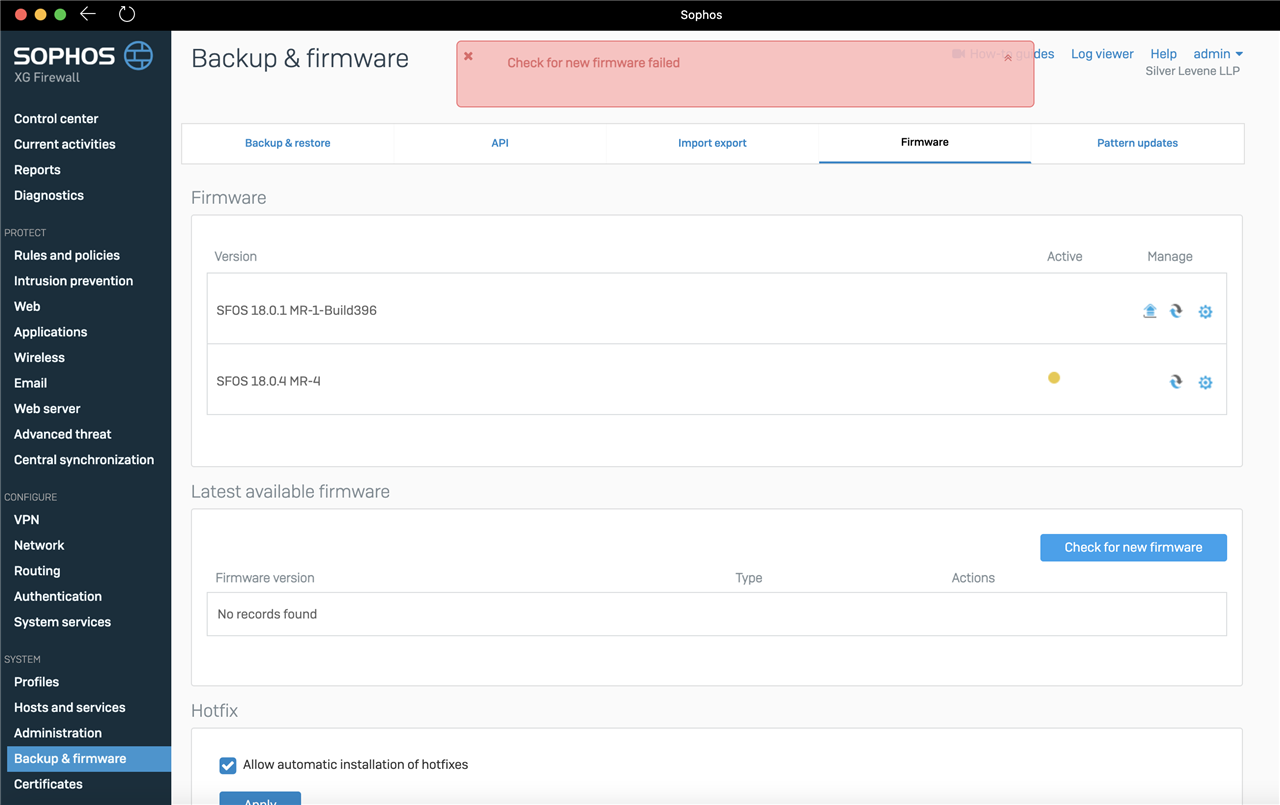
I am unable to upgrade my XG 330 to 18.0.3 MR3 or 18.0.4 MR4. It is currently on 18.0.1 MR1.
Following an upgrade, all XG functionality to contact Sophos fails, this includes licence checks, firmware checks, pattern checks, etc.
So far I have tried updating in-place, manually downloading the firmware and pattern updates, and more recently, re-imaging the XG with 18.0.3 MR3 and then restoring the latest backup. This also failed, so I had to re-image it back to 18.0.1 MR1 in order to regain functionality.
The relevant errors in the u2d.log are:
DEBUG Dec 27 17:26:35 [8563]: --serial = C330XXXXXXXXXXX
DEBUG Dec 27 17:26:35 [8563]: --deviceid = xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
DEBUG Dec 27 17:26:35 [8563]: --fwversion = 18.0.4.506
DEBUG Dec 27 17:26:35 [8563]: --productcode = CN
DEBUG Dec 27 17:26:35 [8563]: --model = XG330
DEBUG Dec 27 17:26:35 [8563]: --vendor = WP02
DEBUG Dec 27 17:26:35 [8563]: --pkg_ips_version = 3.16.06
DEBUG Dec 27 17:26:35 [8563]: --pkg_ips_cv = 16.0
DEBUG Dec 27 17:26:35 [8563]: --pkg_atp_version = 1.0.0334
DEBUG Dec 27 17:26:35 [8563]: --pkg_atp_cv = 1.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_savi_version = 1.0.16399
DEBUG Dec 27 17:26:35 [8563]: --pkg_savi_cv = 1.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_avira_version = 1.0.412711
DEBUG Dec 27 17:26:35 [8563]: --pkg_avira_cv = 4.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_apfw_version = 11.0.012
DEBUG Dec 27 17:26:35 [8563]: --pkg_apfw_cv = 1.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_sslvpn_version = 0
DEBUG Dec 27 17:26:35 [8563]: --pkg_sslvpn_cv = 1.01
DEBUG Dec 27 17:26:35 [8563]: --pkg_ipsec_version = 2.0.001
DEBUG Dec 27 17:26:35 [8563]: --pkg_ipsec_cv = 1.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_geoip_version = 2.0.001
DEBUG Dec 27 17:26:35 [8563]: --pkg_geoip_cv = 1.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_clientauth_version = 1.0.0019
DEBUG Dec 27 17:26:35 [8563]: --pkg_clientauth_cv = 2.00
DEBUG Dec 27 17:26:35 [8563]: --pkg_redfw_version = 3.0.002
DEBUG Dec 27 17:26:35 [8563]: --pkg_redfw_cv = 2.00
DEBUG Dec 27 17:26:35 [8563]: --oem = Sophos
DEBUG Dec 27 17:26:35 [8563]: --central_mgmt = 1.0
DEBUG Dec 27 17:26:35 [8563]: --server = u2d.sophos.com
DEBUG Dec 27 17:26:35 [8563]: --port = 443
DEBUG Dec 27 17:26:35 [8563]: Added new server : Host - u2d.sophos.com, Port - 443
DEBUG Dec 27 17:26:35 [8563]: Final query string is :
DEBUG Dec 27 17:27:08 [8563]: Response code : 0
DEBUG Dec 27 17:27:08 [8563]: Response body :
DEBUG Dec 27 17:27:08 [8563]: Response length : 0
ERROR Dec 27 17:27:08 [8563]: Response not parsed successfully.
ERROR Dec 27 17:27:08 [8563]: FATAL : Error in parsing response, exiting.
csc.log:
Get Request Mode:27 MIGRATION FILE/MODULE NOT FOUND
og_exec: Failed Command: /bin/ipset -D localserviceset 62
syslog.log:
Dec 27 17:26:27 (none) user.err kernel: [ 219.026717] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:27 (none) user.err kernel: [ 219.026731] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:27 (none) user.err kernel: [ 219.042642] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:27 (none) user.err kernel: [ 219.042654] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:27 (none) user.err kernel: [ 219.349938] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:27 (none) user.err kernel: [ 219.349952] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:28 (none) user.err kernel: [ 220.351219] VH index <50> not found in ipset, returning XT_CONTINUE
Dec 27 17:26:28 (none) user.err kernel: [ 220.351232] VH index <50> not found in ipset, returning XT_CONTINUE
Any help on this would be greatly appreciated, as I am just getting a 'never seen this before' and 'no other customers have this issue' from support.
This thread was automatically locked due to age.


