Hello,
I have A Sophos XG at work and a Sophos XG at home. Recently I have acquired a Meraki MX64 that I am running behind my Sophos XG at home. I have been tasked with setting up my work XG with the Meraki MX in a site2site tunnel (for a future deployment). I have the tunnel partially up to where I can connect back to work through a host on the Meraki side without issue. However, I cannot do the opposite. I believe the reason being is that the work XG is trying to pair an IPsec tunnel to my home XG.
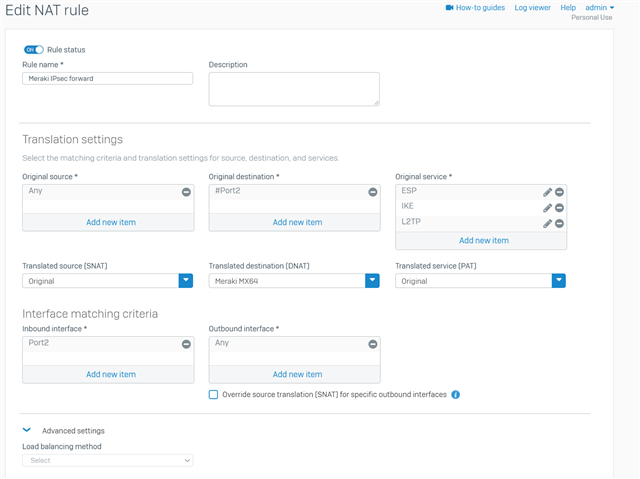
I have created a DNAT and access rule to the Meraki for IKE, ESP and even l2pt to point to the Meraki. However, I do not see these rules being hit what so ever in NAT or access rules. I have other NATs to my file server working fine so I'm not sure if I'm missing some here?
This thread was automatically locked due to age.