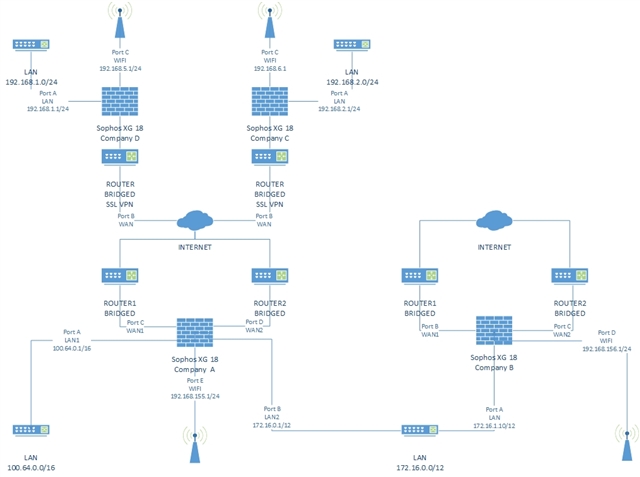
Hi, and sorry for my poor english.
I have 2 Sophos XG 18 connected to LAN with the same Switches. The first Sophos (Intel Hardware) have 2 WAN + 1 LAN (172.16.1.10/12) + 1 WIFI (192.168.100.1/24) the second sophos (vmware) have 2 WAN + 2 LAN (100.64.0.1/16 and 172.16.1.9/12 + 1 WIFI (with some AP55 + 5 SSIDs) + 4 VPN SSL with 3 remote offices. The new Sophos XG works fine, can I see all networks, VPNs to LAN1, VPNs to WAN, some WIFIs SSIDs to VPNs and LAN1... now I have connected the two Sophos with a IPSec Site-to-Site Tunnel, and obiusly, the LAN2 in the Second Sophos are set to None.
I'm trying and read all posts in this community to set the LAN2 Interface to IP 172.16.1.9/12 to remove the IPSec Tunnel, 1.- Add new Zone (LAN2), 2.- Assign LAN2 Zone to interface PORT B, 3.- Assign Static IP to PORT B (172.16.1.9), 4.- Save changes... I see the Network 2 (172.16.0.0/12) from Sophos, but not from VPNs and WIFIs, from first Sophos can't see the Network 1 (172.16.0.0/16)... i'm writing Firewall rules: source LAN, LAN2, VPN destination LAN, LAN2, VPN Accept, we write a Sophos 1 route to see the Sophos 2 network: destination 100.64.0.0/16 Gateway 172.16.1.9 interface (none) metric 0... and nothing seems work, only the IPSec Tunnel.
The offices has to access to some resources in the 172.16.0.0/12 network, and this network has to access to some resources of 100.64.0.0/16 network.
Anyone can help me please?
Thx for advance
This thread was automatically locked due to age.