I'm afraid this question has already been asked but I couldn't find it for XG. I did find it multiple times for UTM but that unfortunately doesn't bring me to a solution.
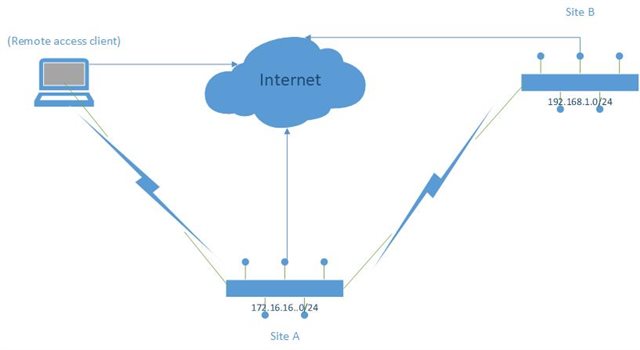
I have to sites, A and B interconnected by a IPSEC VPN connection. Traffic is flowing as expected and everything works fine.
Connected to site A I have SSL VPN remote access clients that can communicate to site A without problem. So far everything is fine.
Now I want to allow remote SSL clients from site A to communicate to site B and it has to be done with a SNAT rule since the other side doesn't want to add the SSL subnet to the tunnel. So basically the remote SSL traffic should be source natted to a site A's local address before being sent to site B.
I made a drawing of the situation:
I made the following firewall rule:
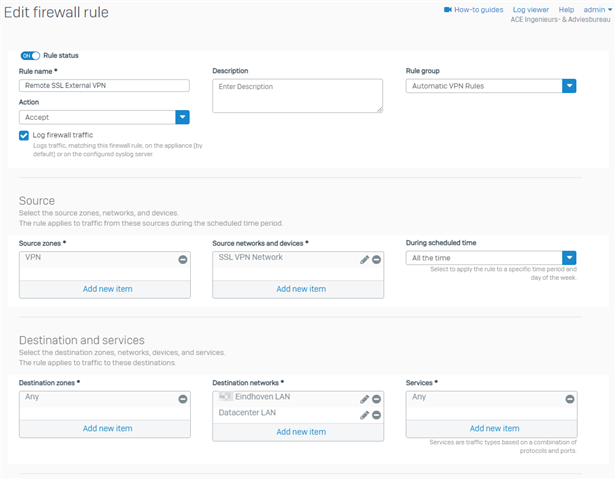
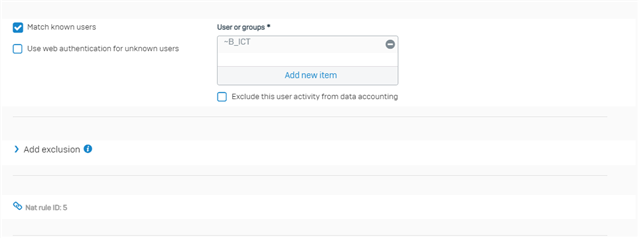
The corresponding NAT rule is the following:
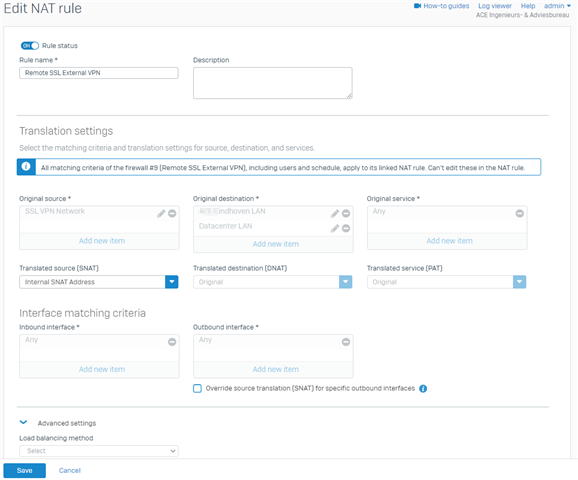
The Translated source (SNAT) address is 172.16.16.250 which is inside the LAN-network of site A.
The SSL VPN Network is: 10.81.234.0/24
VPN config looks like this:
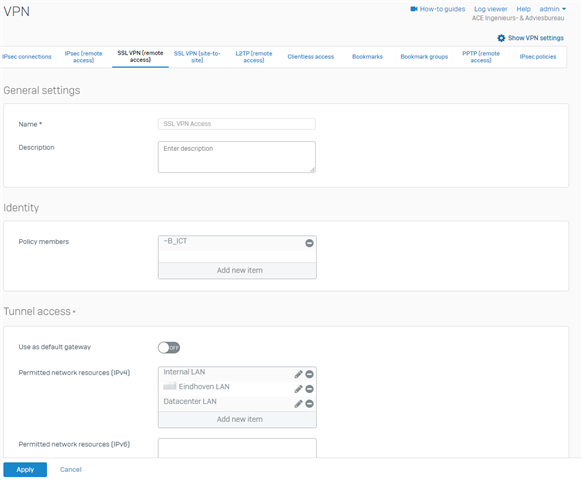
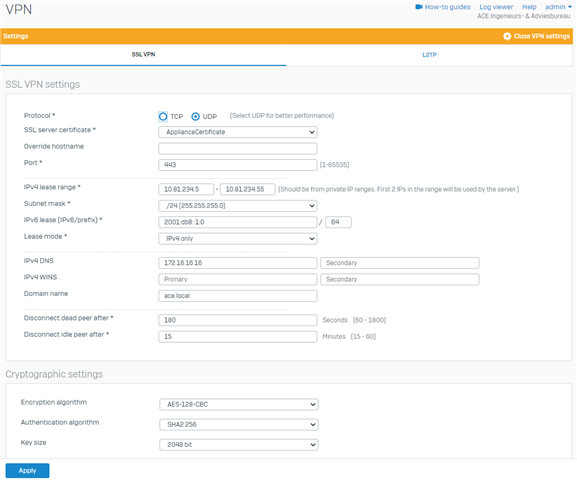
I can "see" the traffic on the XG en it seems that it is being sent to the correct location (however it uses Port2 as Out interface where I expect it should be ipsec0 so this might be the real problem....
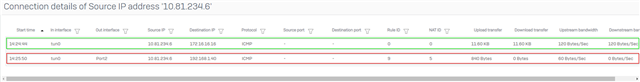
The upper line works and is traffic from the SSL client to the network at Site A. The lower line doesn't get a reply back (it uses Port2 to send the packet out and might need to be ipsec0 interface).
I must be miissing something most likely how to make sure the traffic from the remote access vpn client uses ipsec0 as outgoing interface instead of Port2, but I can't seem to find how to configure this.
Can anyone help me on this one?
This thread was automatically locked due to age.


