Hey there,
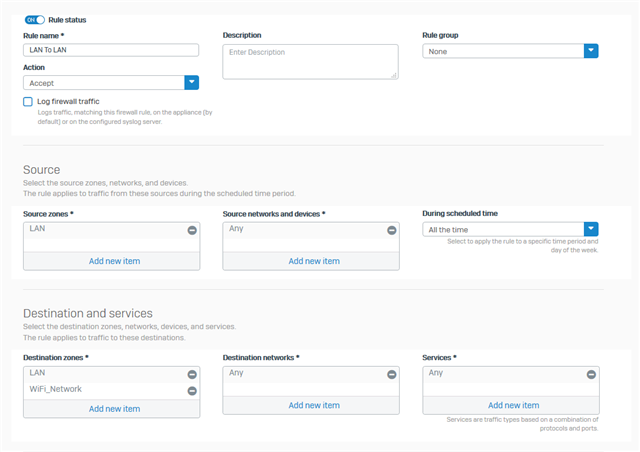
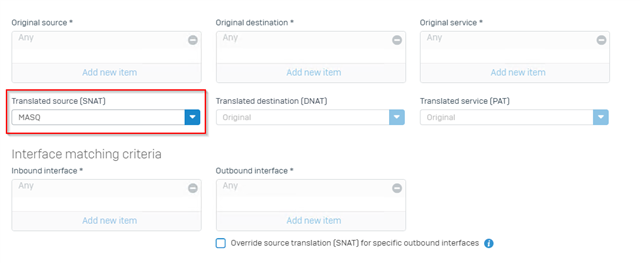
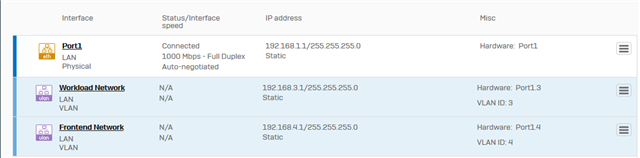
I set up two VLANs. VLAN 3 and VLAN 4. I can ping the gateway for both of the IPs, but can't ping all the IPs on them from the main subnet on the interface that the VLANs were created on. The difference is, the gateway and cisco switch everything is plugged into CAN ping those IPs. I'd really appreciate someone pointing me in the right direction here since I'm sure it's not a firewall rule issue since I tried making rules and checking firewall logs and didn't find anything.
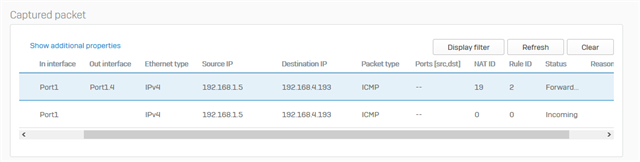
Packet Trace: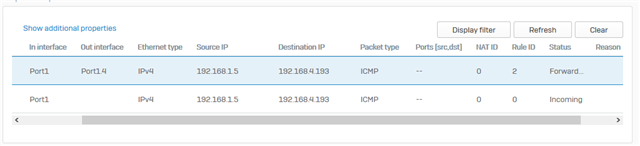
| Ethernet header |
| Source MAC address: |
| Destination MAC address: |
| Ethernet type IPv4 (0x800) |
| IPv4 Header |
| Source IP address:192.168.1.5 |
| Destination IP address:192.168.4.193 |
| Protocol: ICMP |
| Header:20 Bytes |
| Type of service: 0 |
| Total length: 60 Bytes |
| Identification:15073 |
| Fragment offset:0 |
| Time to live: 127 |
| Checksum: 31177 |
| ICMP Header: |
| Type: 8 |
| Code: 0 |
| Echo ID: 1 |
| Echo sequence: 951 |
| Gateway: 0 |
| Fragmentation MTU: 0 |
This thread was automatically locked due to age.