Hi folks,
I have been trying to get a hairpin firewall rule and NAT for my NTP server.
After two failed attempts at using existing devices as NTP sources I built a Raspberry PI-4 which I have tested with Mac min and W10 devices and all update correctly.
Now the issue with the rule processing order
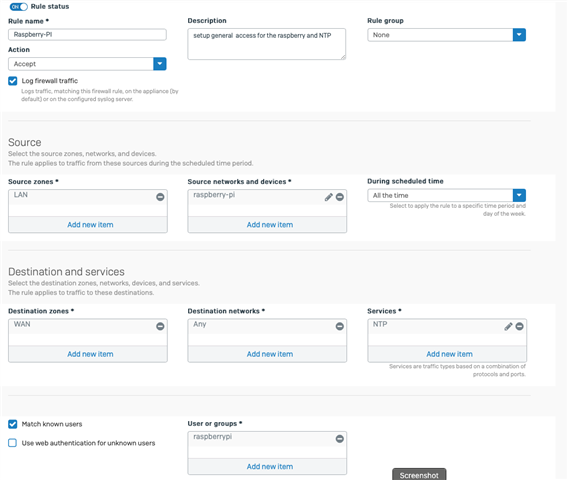
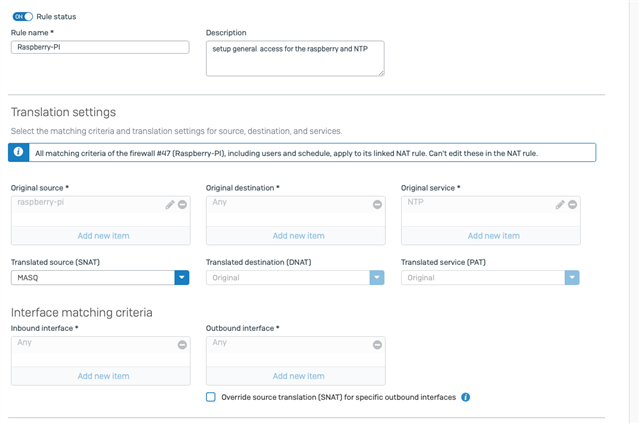
1/. I have high up the firewall rule list a rule for the PI-4 NTP port and linked NAT which works very we'll.
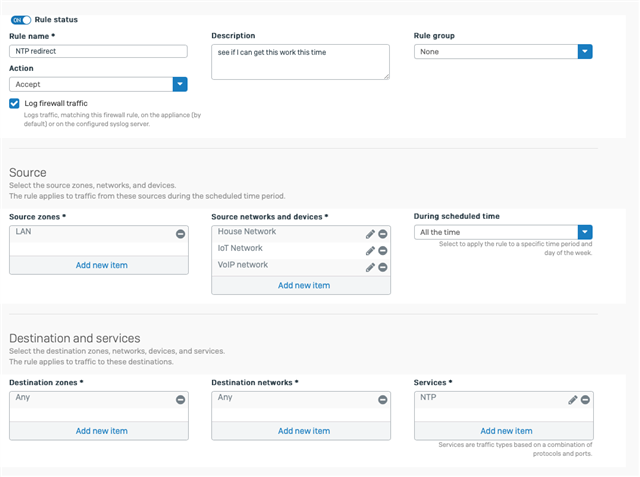
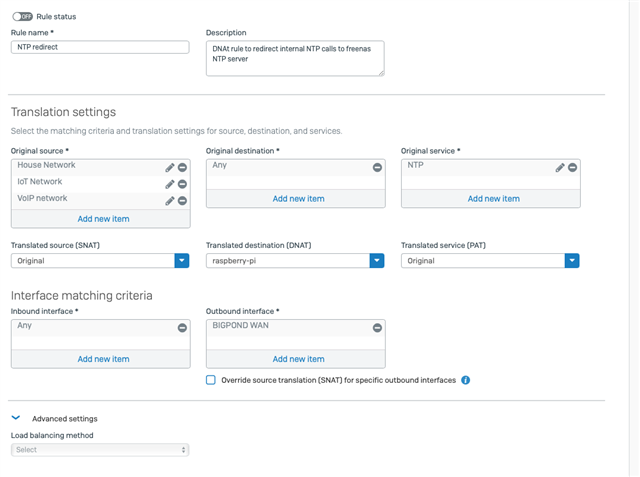
2/. At the bottom of the firewall list I have a general access to the NTP devices using the default NAT policy also works well.
The issue comes when I enable the hairpin NAT which is below the linked NAT in the order, the PI-4 start using the hairpin NAT and talks to itself, also some devices talk to the PI-4 and get responses.
So, the question is why does the PI-4 use the hairpin NAT and not the linked NAT?
Ian
This thread was automatically locked due to age.