I'm a bit stumped on this one. Please see below for current topology.
Windows 10 PC with VMware Workstation Pro installed
- ESXi 6.0 VM within VMware Workstation
- Quad port Intel NIC installed on Windows 10 PC
- Using Virtual Network Editor, I have bridged Ethernet adapters to their perspective port on Intel NIC
- Within ESXi, NICs are showing up and showing up in vSphere
- Sophos XG virtual appliance VM deployed, and firewall is already configured
This is what my networking looks like within VMware
I created a separate vSwitch for the WAN interface and pointed it vmnic2, and vSwitch0 is being used as the LAN interface of the firewall.
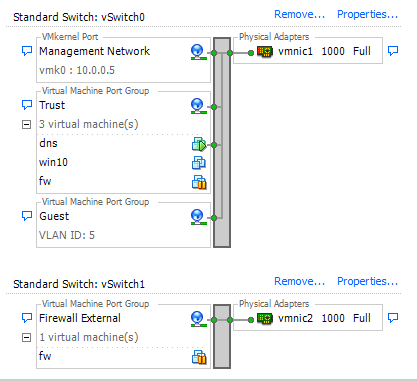
I've been doing a lot of researching, but there's not a whole lot posted on what I'm trying to do here.
Does the LAN interface of the XG need to be on it's own vSwitch as well, or can this be shared with the vSwitch0? I also have a VLAN 5 interface (Guest) on the XG that I've configured off the LAN interface, but I can't talk to it when everything is connected. I've done all the necessary tagging between switches and firewall rules. Does there need to be some sort of static route, or does tagging within vSphere networking?
I also use the Windows 10 machine as my workstation too, using the onboard NIC for network connection. Is what I'm trying to do possible?
This thread was automatically locked due to age.
