Hi all,
i try at different XG's and different versions 18.0.3 and 18.0.4 to use the standard-proxy-mode.
(my last question "How to allow Standard-Proxy connections only" suggests that the configuration is correct. )
Today i do the test again ... very simple ... but without success:
I allow Port 3128 only () and configure 3128 at the Browser ... of course.
Block all other traffic from this PC.
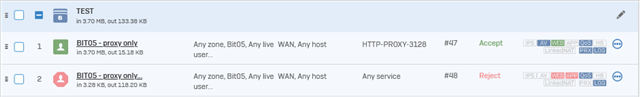
Firewall and webproxy logs show "allow" for the request. But page is not loaded:
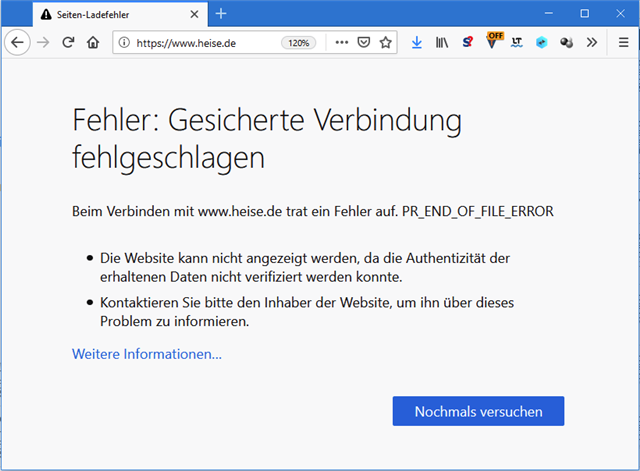
Someone got this running? How?
Thanks!
This thread was automatically locked due to age.
