Hi,
Since upgrading to V18 where NAT and Firewalls have been separated. How would I be sure to fully block and Drop a malicious WAN address traffic from hitting our web facing services?
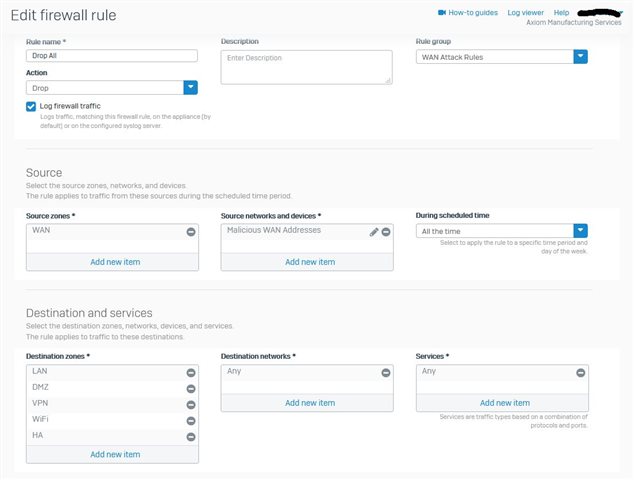
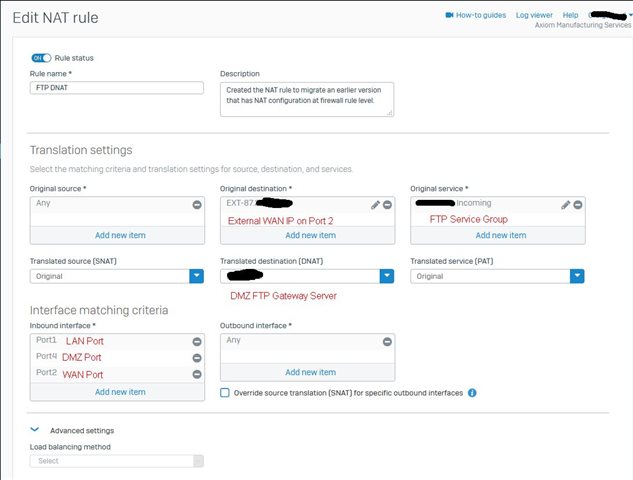
I have written a drop rule containing a list of IP Addresses as sources from WAN zone and placed it at the top of my firewall rules, but I'm still seeing Allowed traffic against my Port Forwarding Rules (example shown)
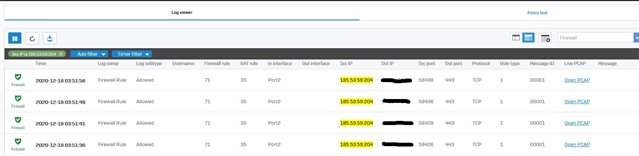
Do I also need to write a specific NAT rule to block these malicious WAN IPs? If yes what would this look like?
Thanks,
Craig
This thread was automatically locked due to age.