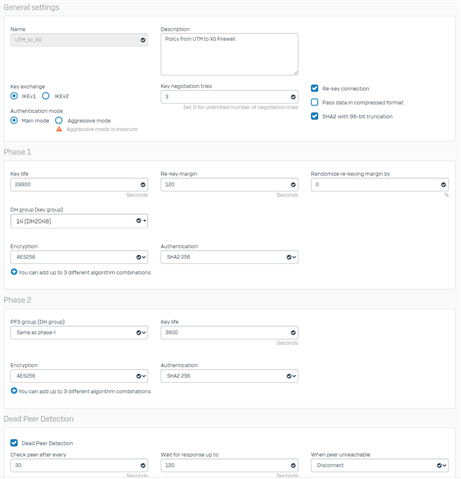
Hello Community,
I have a strange problem. I have a successfully established IPsec connection between an UTM and a XG firewall. Both products have the latest firmware: UTM with 9.705-3 and the XG with SFOS 18.0.3 MR-3. The IPsec connection is established exclusively via IPv6.
When I send a ping from the XG to a server in the zone of the UTM, I have 100% packet loss - tested via "Diagnostics" -> "Tools" -> "Ping". If I test the address via "Diagnostics" -> "Tools" -> "Route lookup", it also says correctly: "IPv6 is located on the ipsec0. IPv6 is not behind a router".
If I use a ping from the UTM to a server in the XG network via "Support" -> "Tools" -> "Ping Check", all pings arrive (0% packet loss). Only when the ping from the UTM to the XG was successful can I now also ping successfully from the XG to the UTM. However, this only works for about 5 to 15 minutes (if no other traffic is active via the IPsec tunnel during this time). After that, no connection is possible from the XG to the UTM. Only when I send a ping from the UTM to the XG does it work again temporarily.
I have been trying for days to find out where the error is, with the XG or with the UTM, and have also tried to enter static routes, unfortunately without success. What have I overlooked or where do I have to look to find the error?
Greetings
Jan
This thread was automatically locked due to age.