Hello,
I have been slowly making everything work with SSL/TLS inspection. Trying to get as much as possible inspected and adding exclusions for things that I have not been able to find how to fix.
But I got to an impasse with two applications, that have the same issue. I feel I have something wrong in my settings but here it goes.
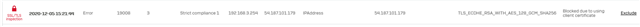
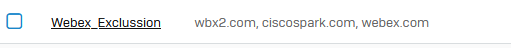
1) Webex. I have a rule to just pass *.webex.com. But for some reason some of the connections are going to an IP and XG is not reverse resolving such IP's. I can reverse resolve the IPs elsewhere and I get a webex domain. (I seldomly need to use webex so I have been disabling TLS inspection when I need it)
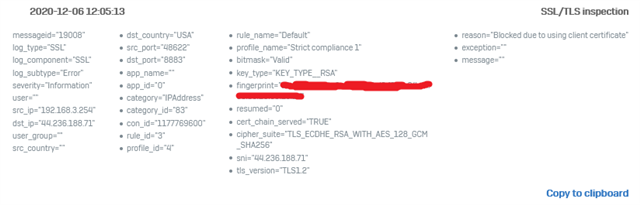
2) the reason I wrote today is becasuse of this problem. I have a new device that is tryign to contact aws server. Again the logs show multiple IPs so I do not know how I would be able to exclude each one of them. See the image of this capture.
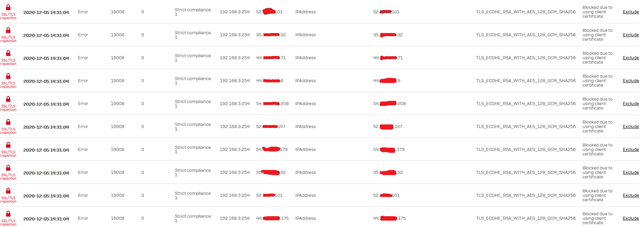
The big issue is that the device is sending thousands of DNS queries per hour (about 1M in 12 hrs) trying to desperately connect to their home.
any ideas, direction would be greatly appreciated.
I am using SFVH (SFOS 18.0.3 MR-3)
Thank you
This thread was automatically locked due to age.