Hi,
In my test Environment i saw when i run apt-get update && upgrade on my two linux servers (Debian and Ubuntu) that the malware and content scanning was blocking the sources.list urls:
deb http://ftp.debian.org/debian buster main contrib non-free
deb http://ftp.debian.org/debian/ buster-updates main contrib non-free
deb http://security.debian.org/ buster/updates main contrib non-free
deb archive.ubuntu.com/.../ focal main restricted
deb security.ubuntu.com/.../ focal-security main restricted
This is a new behavior for the XG v18 and must have come with MR3 update. I remember that this was working in MR1.
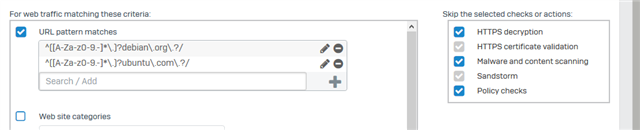
My workaround was to manually create web exeptions for those URLs but i cannot se why the sophos v18 MR3 detects those apt sources as malware by default. This will be a problem for all linux servers when they need to update. I have opened all the urls from sources.list in a webbrowser, and the site loads, but just shows a blank page with no message.
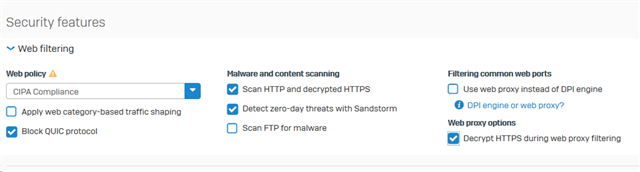
My webfilter is not strict and i have tried to disable that webfilter, but it will return with the same error/false positive. The thing is that malware and content scanning in blocking.
The only way to fix this is to disable the Malware and content scanning under the firwall rule OR create an web exeption for those url's above. I can see some blocks in the webfilter firewall for security... logs, but most are allowed to thoese URL's. The thing is that the apt-get update start to loop on GET1, GET2, GET3, GET1, GET2, GET3.... And the only way to see this error is to surf to the site and get a blank page or disable things and it starts to works again. Strange error :(
I can see that this is a false positive (badly).
Anyone else who have had this? Any ideas how to fix this without exeptions?
Regards,
This thread was automatically locked due to age.