Hi,
I am having some major issues working out why some of my packets are being classed as INVALID_TRAFFIC on my Sophos XG210.
A bit about my set up...
I have an XG210 acting as a perimeter firewall, and is also the gateway for my DMZ zone. I have an XG450 that is acting as my LAN firewall. DMZ interfaces on both firewall pairs are connected to a stack of DMZ switches. The Aruba stack also have a tagged port passing DMZ traffic via our Core to our TORs and our VMWare environment.
The LAN firewall also has a LAN interface configured to our LAN Core switch.
Static routing on my Core switch routes all traffic through to the XG450s.
Rules are configured on the XG450s allowing specific IPs/Services from the LAN through to the DMZ. Static routing is set up passing the traffic to the XG210s out of the DMZ interface (via the Aruba stack)
Rules are configured on the XG210 allowing LAN IP ranges to the DMZ IP ranges.
I have two VMs, one configured with a LAN IP and the other with a DMZ IP.
From the DMZ VM, I can ping the gateway (DMZ Firewall, and also the LAN firewall, and every server in the LAN – temporarily by design whilst I troubleshoot this issue). I see packet captures hit correct rules, and everything seems fine.
However, from the LAN VM I cannot ping the DMZ VM. I can ping the DMZ gateway but when running a packet capture, it seems that I am not seeing any ICMP echo requests, but only replies – which are then classed by the DMZ firewall as INVALID_TRAFFIC.
I put wireshark on the LAN VM and it seemed the ICMP response was hitting my core and then not getting a reply. However, the LAN firewall packet capture sees the incoming packet and shows it as allowed and passed to the DMZ firewall. The DMZ firewall only shows the echo reply.
I have no idea why this is happening, and why it is happening only one way. Can someone please put me out of my misery!
Some packet captures to hopefully help…
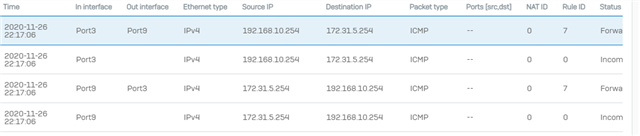
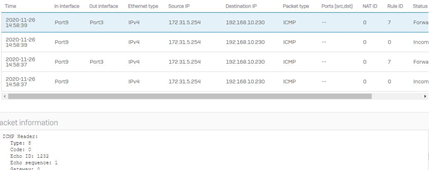
Packet Capture on the LAN firewall – showing the LAN source pinging (ICMP type8 – request) the DMZ destination. So the ping is hitting the LAN firewall…
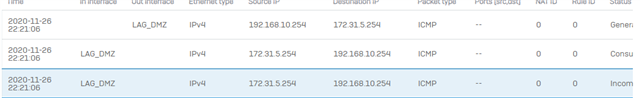
Packet Capture on the DMZ firewall – not seeing the LAN source address, but instead seeing the DMZ source address and the ICMP header at type 0 (reply)
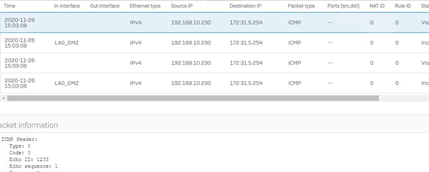
Successful pings from the DMZ server (via the DMZ interface) pinging the LAN VM and the DMZ VM
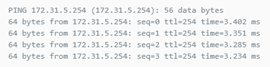
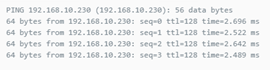
So the routing on the DMZ side are fine...the packet goes the way its meant to and hits all of the correct rules. It just seems that the LAN-DMZ routing/filters/rules is wrong or misconfigured somewhere - but I just can't see where?!
For testing purposes I have made the rules fairly open - LAN->DMZ and DMZ-LAN are open for any ranges and any services, but this INVALID_TRAFFIC tells me it is something before it even gets to the rule filtering.
Any help or suggestions would be greatly appreciated, and if there is any more info I can give to help people help me then just let me know!
Thanks in advance to anyone who can help!
This thread was automatically locked due to age.