I am troubleshooting AD single sign-on with my XG Firewall V18 MR3
I have found this in the help section, please can someone explain what the Firewall Rule mentioned in the Red Box in the screenshot below should consist of?
I have no rules which allow NTLM/Kerberos Traffic, so will need to create one, along with a NAT rule I suspect.
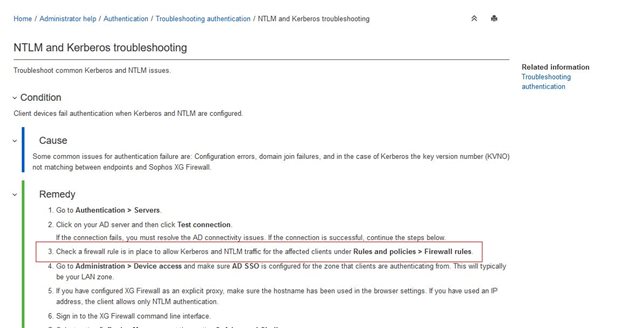
I want my internal Clients to Authenticate with AD SSO, so I imagine this rule mentioned above directs NTLM/Kerberos traffic back to the Domain controllers?
STAS is so flaky I want to try this instead.
Any advice appreciated.
Thanks,
Craig
This thread was automatically locked due to age.

