This question seems to come up in the forums in the past, but I am not finding a solution to my issue.
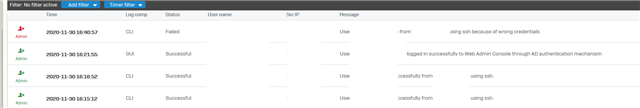
User '-' failed to login from 'x.x.x.x' using ssh because of wrong credentials
XG Admin log file shows me that many (not all) internal Windows clients are attempting this. No outside sources (yet?). Each client is attempting this once approximately every 24 hours. Each one has different times compared to other clients and the time does not match the clients boot up time. It is only listed once in the log for each attempt: I can reproduce the log entry by using putty and entering in the IP address of the XG unit and simply quit putty without entering a name. If I press Enter through the name prompt and enter anything for password, I get two entries in the XG's log. I have the latest firmware available installed in this unit.
I have scanned each client for Malware, but nothing found. Any ideas how I can locate the source of this? I had a different network act similar, but those log entries stopped about a month ago after a firmware update to 18.0.3 MR-3. Coincidence probably??
Any way to find out what is causing this?
This thread was automatically locked due to age.