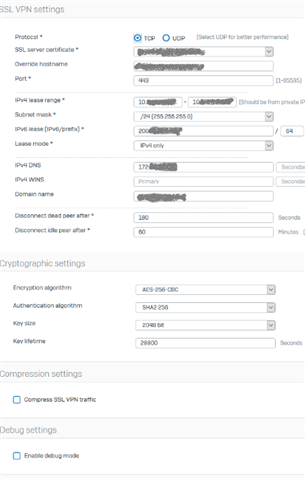
Hey together,
Simple Question: Does the XG supports VPN access with SSL or IPSec VPN and IPv6 ?
Background: We have several users which must use a WAN connection from Unitymedia or Vodafone (cable based) in their homeoffice.
The issue is, that these carriers are using DS-Lite, which is breaking the SSL VPN connection. No vpn connection is possible.
As a workaround we could use IPv6 VPN, if it possible with the XG. I didn't find any useful information regarding the documentation.
If there any other solutions, i'm happy for any ideas.
Regards,
Jonny
This thread was automatically locked due to age.