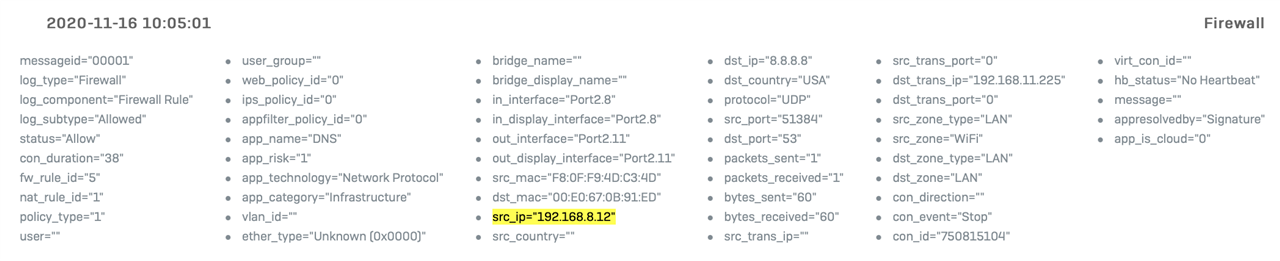
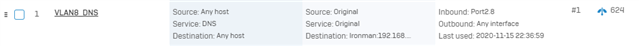
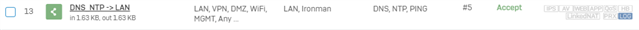
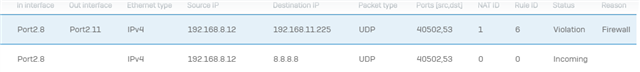
I want IoT devices to use my internal DNS server. I setup a NAT rule to translate inbound DMZ interface to destination internal DNS server and I have a matching firewall rule but the traffic is getting dropped.
IoT device calls to 8.8.8.8 on Port 53 and the NAT rule translates correctly but XG fails to match the firewall rule even though it matches the log message details exactly.
Could this be a bug, possibly the order of operations, or am missing something in my setup?
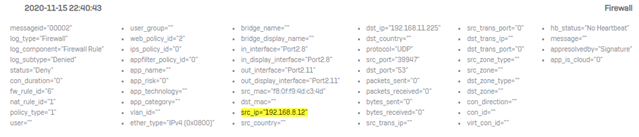
2020-11-15 22:21:31Firewallmessageid="00002" log_type="Firewall" log_component="Firewall Rule" log_subtype="Denied" status="Deny" con_duration="0" fw_rule_id="6" nat_rule_id="1" policy_type="1" user="" user_group="" web_policy_id="2" ips_policy_id="0" appfilter_policy_id="0" app_name="" app_risk="0" app_technology="" app_category="" vlan_id="" ether_type="IPv4 (0x0800)" bridge_name="" bridge_display_name="" in_interface="Port2.8" in_display_interface="Port2.8" out_interface="Port2.11" out_display_interface="Port2.11" src_mac="f8:0f:f9:4d:c3:4d" dst_mac="" src_ip="192.168.8.12" src_country="" dst_ip="192.168.11.225" dst_country="" protocol="UDP" src_port="42410" dst_port="53" packets_sent="0" packets_received="0" bytes_sent="0" bytes_received="0" src_trans_ip="" src_trans_port="0" dst_trans_ip="" dst_trans_port="0" src_zone_type="" src_zone="" dst_zone_type="" dst_zone="" con_direction="" con_id="" virt_con_id="" hb_status="No Heartbeat" message="" appresolvedby="Signature" app_is_cloud="0"
Packet Capture
This thread was automatically locked due to age.