Hey together,
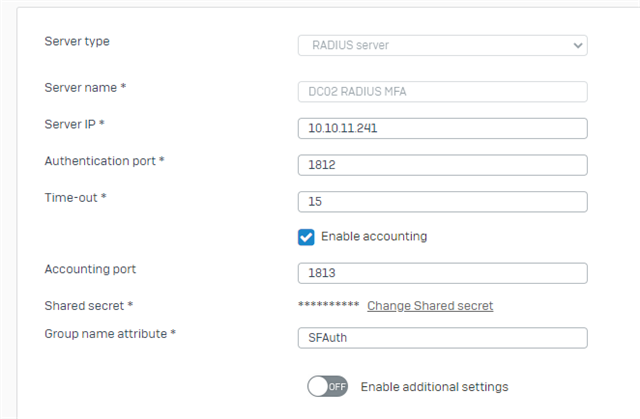
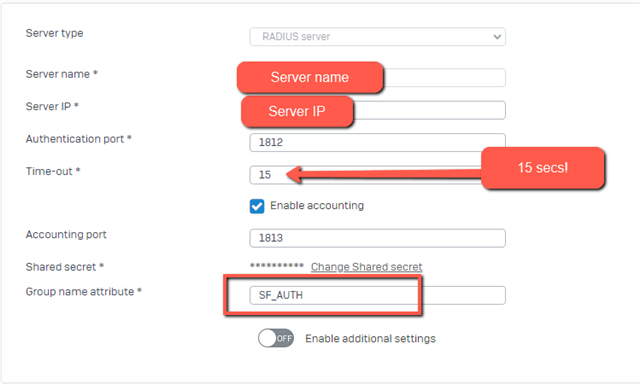
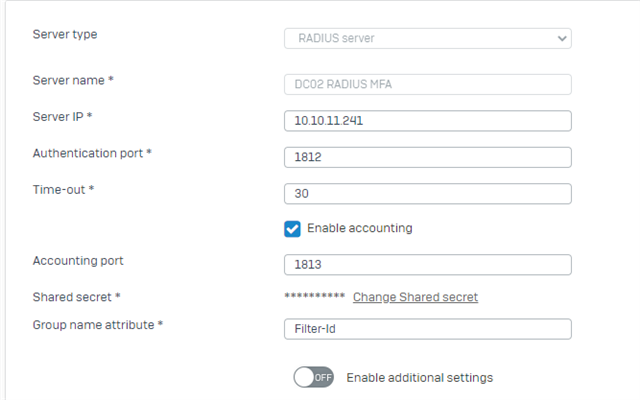
I've configured our NPS according the tutorial from twister5800 https://community.sophos.com/xg-firewall/f/recommended-reads/122575/sophos-xg-using-azure-mfa-for-ssl-vpn-and-user-portal/451795#451795 .
The general authentication is working but I have several configurations issues. Maybe somebody can assist.
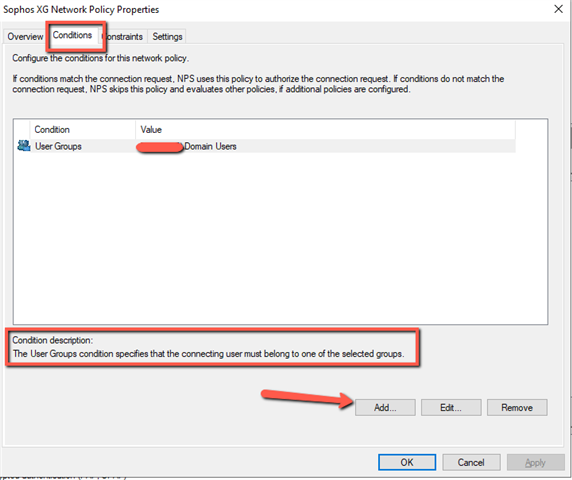
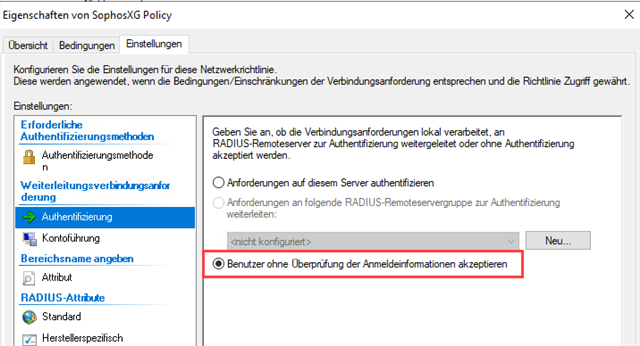
- The authentication is only working if I switch to "Accept user without confirming their credentials" instead of "Authenticate requests on this Server". Otherwise the autentication fails. The NPS is installed at a domain controller.
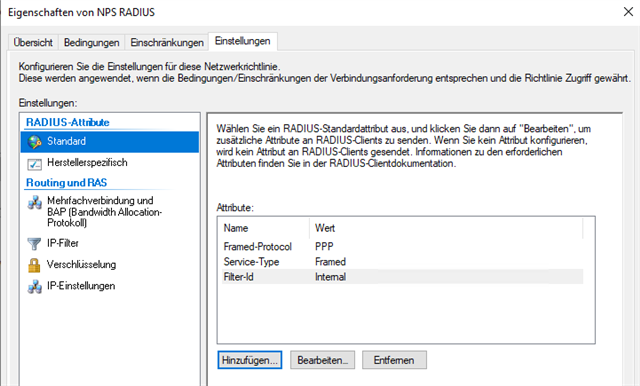
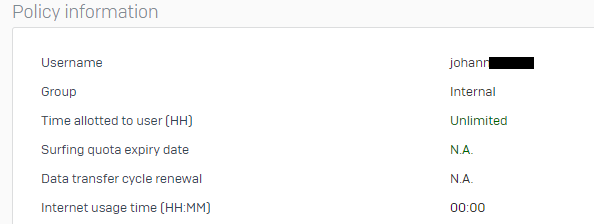
- How can I control the group membership of the users? If I login at the user portal, they user is dropped to the default group at XG.
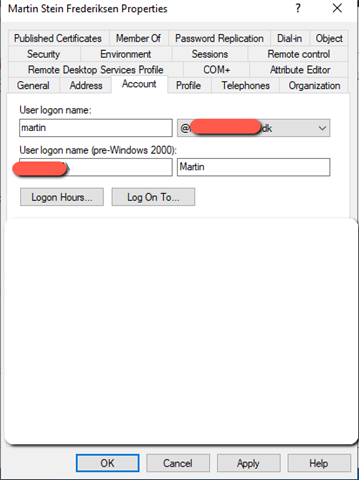
- If I login with the upn at the user portal, the user is created without the domain ending. Like max.mustermann instead of max.mustermann@company.
This is not happening if I login with he the regular active directory login,where the user is created with full upn.
Happy for any support.
This thread was automatically locked due to age.