I have a problem with two XG 106 on SFOS 18.0.3
Both have a routing-based IPsec to another virtualized XG with SFOS 18.0.3
Both XG 106 are connected to VDSL lines with variable IPs and every night the XGs change IP.
Unfortunately after the IP change the tunnels come up again but the tunnel interfaces stay down and the XGs seem not to notice it.
Only a restart of the IPsec tunnels on the hardware XGs does reactivate the interfaces properly.
Alternatively through SSH console the restart of the VPN service.
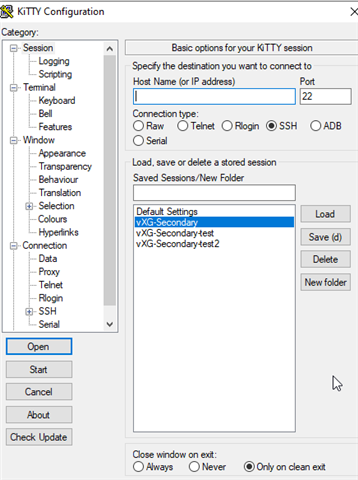
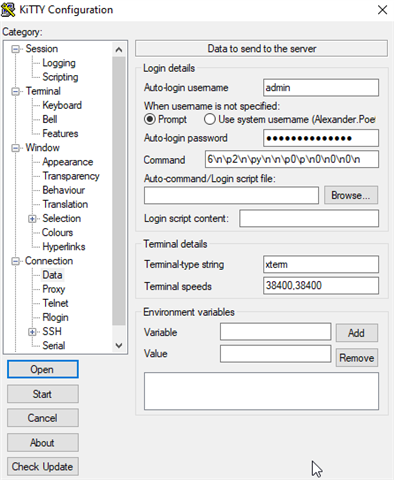
On this basis I tried creating a script that uses PLINK to autmatically connect to the XGs and restart the VPN service.
Unfortunately, it looks like the scripted acces does work differently from the normal putty access.
On the putty session after login I get the menu options and then it's option 6, then option 2
Unfortunately when I try and script this with plink it doesn't work.
I get an "access granted" but from the logs I notice that I do net get a menu put apparently just a shell/command
And the passing of the "6" parameter just returns an error.
Here the screenshot from the session.
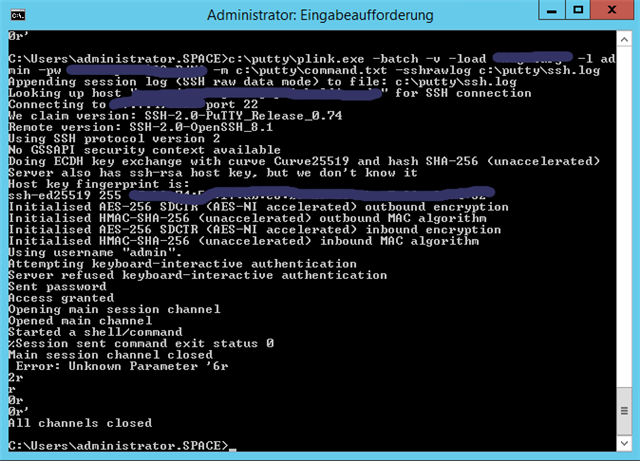
Apparently the session is beeing closed even before the first parameter is sent.
Is there a way to do this properly?
This thread was automatically locked due to age.